Table of Contents
Enroll in Entri’s AI-Powered Cybersecurity course now!
What Is an Incident Response Specialist?
An Incident Response Specialist protects organizations from cyber attacks. This professional handles active security incidents. The main goal is damage control. The specialist reduces impact and restores systems. Quick decisions are often required. Strong technical knowledge guides actions. Clear thinking improves investigation accuracy. The role demands responsibility and focus.
Core Purpose of the Role
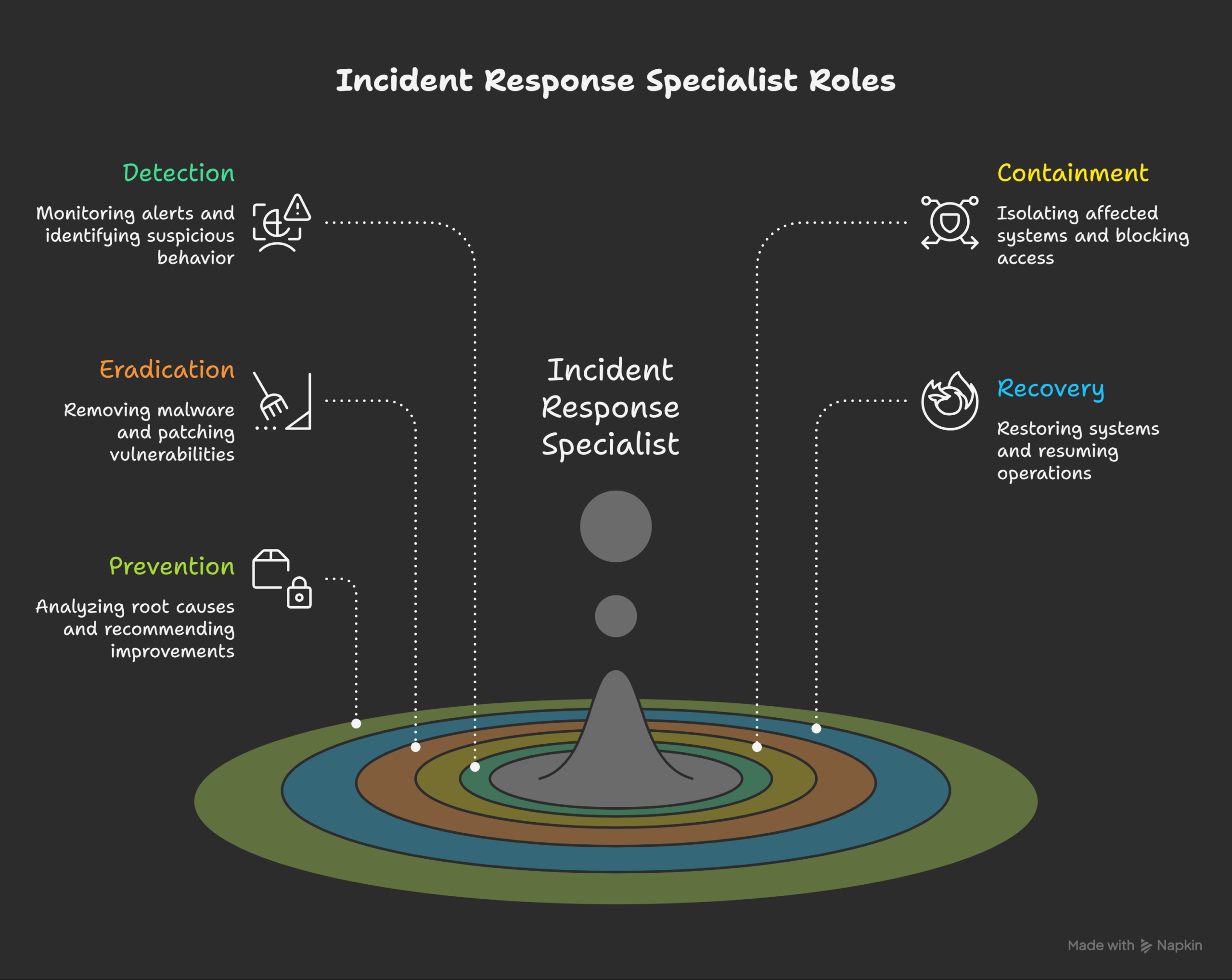
An Incident Response Specialist manages the incident lifecycle. The lifecycle follows structured phases. Each phase has clear objectives.
Main objectives include:
-
Detect security incidents early
-
Monitor alerts continuously
-
Identify suspicious behavior
-
-
Contain active threats quickly
-
Isolate affected systems
-
Block malicious access
-
-
Eradicate attack elements
-
Remove malware artifacts
-
Patch exploited vulnerabilities
-
-
Restore normal operations
-
Recover clean backups
-
Validate system integrity
-
-
Prevent future incidents
-
Conduct root cause analysis
-
Recommend security improvements
-
Key Responsibilities
The role combines technical and analytical tasks. Daily work depends on threat severity.
| Responsibility | Description | Outcome |
|---|---|---|
| Alert Analysis | Review security alerts | Identify real threats |
| Investigation | Analyze logs and evidence | Determine attack source |
| Containment | Limit attacker movement | Reduce damage impact |
| Recovery | Restore affected systems | Resume business operations |
| Reporting | Document findings clearly | Improve future defense |
Each responsibility requires structured action. Documentation remains extremely important. Reports guide management decisions. Accurate records support compliance requirements.
Where They Work
Incident Response Specialists work across industries. Demand exists in multiple sectors.
-
IT companies
-
Financial institutions
-
Healthcare organizations
-
Government agencies
-
Large enterprises
Most professionals work in Security Operations Centers. Some join consulting firms. Others work as internal security team members.
Work Environment and Pressure
Incidents often occur unexpectedly. Some cases require immediate attention. Time pressure increases during major breaches. Calm behavior improves response quality. Team collaboration remains essential. Communication with leadership happens regularly.
Skills in Action
Technical knowledge drives investigation steps. Analytical thinking connects attack patterns. Logical reasoning supports containment decisions. Documentation ensures transparency. Continuous learning keeps skills updated.
An Incident Response Specialist acts as a digital firefighter. The mission focuses on minimizing risk. The role protects data and reputation. Strong dedication defines long term success.
Skills Required for Incident Response
Incident response demands strong technical foundations. Analytical thinking strengthens investigation quality. Practical skills improve decision accuracy. Clear communication supports effective coordination. Continuous learning keeps professionals updated. Each skill contributes to faster containment. Balanced development ensures long term success. Mastery develops through consistent practice.
Technical Skills
Technical expertise forms the core foundation. Strong fundamentals reduce investigation errors.
1. Networking Knowledge
Understanding network behavior is essential. Attackers exploit network weaknesses.
-
Know TCP and UDP protocols
-
Identify abnormal traffic patterns
-
Detect unauthorized connections
-
-
Understand DNS and HTTP
-
Analyze suspicious domain queries
-
Monitor unusual web requests
-
2. Operating System Proficiency
Systems generate valuable investigation evidence.
-
Windows system knowledge
-
Review Event Viewer logs
-
Analyze running processes
-
-
Linux fundamentals
-
Inspect system logs
-
Monitor active services
-
3. Security Tools and Technologies
Modern investigations require specialized tools.
| Skill Area | Tools Used | Purpose |
|---|---|---|
| Log Analysis | SIEM platforms | Detect suspicious activities |
| Endpoint Security | EDR tools | Monitor device behavior |
| Network Monitoring | IDS/IPS systems | Identify malicious traffic |
| Malware Analysis | Sandbox tools | Examine harmful files |
Tool familiarity increases response speed. Practical exposure improves tool confidence.
Analytical and Investigation Skills
Incident response requires structured thinking. Evidence must guide conclusions.
-
Pattern recognition
-
Identify repeated attack behavior
-
Detect hidden anomalies
-
-
Root cause analysis
-
Trace attack origin
-
Understand exploitation methods
-
-
Risk assessment
-
Evaluate incident severity
-
Prioritize response actions
-
Logical reasoning prevents false assumptions. Evidence based decisions ensure accuracy.
Communication and Documentation Skills
Technical ability alone is insufficient. Clear reporting supports management understanding.
-
Write concise incident reports
-
Explain technical findings simply
-
Provide actionable recommendations
-
-
Collaborate with security teams
-
Share investigation updates
-
Coordinate containment steps
-
Effective communication reduces confusion during crises.
Soft Skills and Professional Traits
Strong personal qualities strengthen performance.
-
Attention to detail
-
Notice subtle system changes
-
Avoid missing critical evidence
-
-
Time management
-
Handle multiple alerts efficiently
-
Meet reporting deadlines
-
-
Adaptability
-
Respond to evolving threats
-
Learn emerging attack techniques
-
Incident response blends technology and mindset. Technical strength enables investigation. Analytical clarity improves containment. Communication builds trust within teams. Continuous improvement sustains long term growth.
6-Month Learning Roadmap
A structured roadmap accelerates career progress. Six months require disciplined learning habits. Daily practice builds technical confidence. Weekly revision strengthens knowledge retention. Consistency matters more than intensity. Clear milestones maintain steady motivation. Each month should focus on goals. Practical exposure must complement theory.
Month 1: Networking Fundamentals
Networking forms the investigation foundation. Strong basics reduce confusion later. Attack patterns often involve networks.
Core topics to cover:
-
OSI and TCP/IP models
-
Understand layered communication structure
-
Identify protocol responsibilities
-
-
Common protocols
-
Study HTTP and HTTPS
-
Learn DNS and DHCP
-
-
Ports and services
-
Recognize standard port numbers
-
Map services to open ports
-
-
IP addressing concepts
-
Practice subnetting basics
-
Identify private and public ranges
-
Practice activities:
-
Capture traffic using packet tools
-
Analyze simple network logs
-
Identify suspicious connection attempts
Networking clarity improves alert investigation accuracy.
Month 2: Operating Systems and System Logs
Incident responders analyze system behavior daily. Operating system knowledge supports evidence collection.
Windows fundamentals:
-
Understand file system structure
-
Explore Windows Event Viewer
-
Identify startup processes
Linux basics:
-
Navigate terminal commands
-
Inspect system log files
-
Manage user permissions
Log analysis focus:
| Log Source | What to Observe | Why It Matters |
|---|---|---|
| Security Logs | Failed login attempts | Detect brute force attacks |
| Application Logs | Unexpected crashes | Identify malware impact |
| System Logs | Privilege changes | Track unauthorized access |
Practice reviewing sample logs daily. Try identifying anomalies manually. Observation skills improve with repetition.
Month 3: Cybersecurity Foundations and Threat Landscape
Understanding threats improves defensive thinking. Attackers follow common patterns. Learning these patterns builds awareness.
Threat categories to study:
-
Malware types
-
Ransomware behavior
-
Trojan infection methods
-
-
Social engineering
-
Phishing email indicators
-
Credential harvesting techniques
-
-
Network attacks
-
Man in the middle attacks
-
Denial of service attempts
-
Security concepts:
-
CIA triad principles
-
Authentication and authorization basics
-
Multi factor authentication importance
Study real breach case summaries. Identify attacker entry points. Understand containment decisions taken.
Month 4: SIEM Tools and Monitoring
Security teams rely on monitoring tools. SIEM platforms centralize log data. Learning these tools increases employability.
Key concepts:
-
Log aggregation process
-
Correlation rules
-
Alert severity levels
Skill development areas:
-
Writing search queries
-
Filter suspicious IP addresses
-
Identify repeated login failures
-
-
Alert triage
-
Differentiate false positives
-
Prioritize critical threats
-
Hands-on focus:
| Skill | Practice Method | Outcome |
|---|---|---|
| Query Writing | Build simple log searches | Faster detection |
| Dashboard Review | Analyze visual alerts | Pattern recognition |
| Incident Tagging | Classify alerts correctly | Organized workflow |
Practice daily alert reviews. Simulate investigation workflows. Document each practice case clearly.
Month 5: Incident Response Process and Forensics Basics
This month focuses on structured response. Incident handling follows clear phases.
Incident lifecycle phases:
-
Preparation
-
Define response policies
-
Understand escalation paths
-
-
Identification
-
Confirm actual incidents
-
Gather supporting evidence
-
-
Containment
-
Isolate compromised hosts
-
Block malicious IP addresses
-
-
Eradication
-
Remove malicious artifacts
-
Patch exploited vulnerabilities
-
-
Recovery
-
Restore systems securely
-
Monitor for reinfection
-
Digital forensics basics:
-
Preserve evidence carefully
-
Maintain chain of custody
-
Capture disk and memory data
Practice writing mock incident reports. Focus on clarity and structure. Structured thinking improves real response efficiency.
Month 6: Advanced Practice and Realistic Simulations
Final month builds real world readiness. Confidence develops through simulations.
Advanced activities:
-
Participate in capture the flag challenges
-
Analyze simulated ransomware scenarios
-
Practice phishing investigation exercises
Build a simple home lab:
-
Install virtual machines
-
Create attack simulation environment
-
Generate sample security logs
Professional preparation tasks:
| Preparation Area | Action Step | Benefit |
|---|---|---|
| Resume Building | Highlight lab projects | Demonstrate practical skills |
| Interview Practice | Review common scenarios | Improve confidence |
| Knowledge Review | Revise core fundamentals | Strengthen retention |
Revise previous months weekly. Focus on weak knowledge areas. Track improvement through self assessment.
Study Discipline and Weekly Structure
Consistency determines overall success. Allocate two focused study hours daily. Dedicate weekends for lab practice. Review notes every Sunday. Document learning progress weekly.
Balance theory and practice equally. Avoid rushing complex topics. Strengthen fundamentals before advancing. Maintain curiosity about evolving threats. Follow cybersecurity news regularly.
A six month roadmap demands commitment. Structured learning builds strong foundations. Practical exposure strengthens technical confidence. Each month adds valuable capability. Clear progression reduces overwhelm. Persistent effort creates job readiness. Focused preparation increases career opportunities. Dedication transforms beginners into skilled responders.
Enroll in Entri’s AI-Powered Cybersecurity course now!
Certifications That Help
Certifications strengthen your professional credibility. They validate structured cybersecurity knowledge. Employers value certified candidates highly. Certifications demonstrate serious career commitment. They also improve interview confidence. Structured preparation deepens technical understanding. However, certification should support practical skills. Balanced preparation ensures real competence.
Why Certifications Matter
Certifications provide standardized skill validation. Recruiters use them as screening filters. Many job descriptions mention certifications clearly. They indicate baseline security awareness. Structured exam syllabi cover essential domains. Preparation encourages disciplined study habits. Certification holders often receive better shortlisting chances.
Key advantages include:
-
Industry recognition
-
Globally accepted credentials
-
Standardized evaluation methods
-
-
Structured learning path
-
Clear syllabus guidance
-
Organized topic coverage
-
-
Career growth support
-
Increased promotion opportunities
-
Stronger salary negotiation power
-
Certifications complement hands-on experience effectively.
Entry-Level Certifications
Beginners should start with foundational credentials. These certifications build strong security basics.
1. CompTIA Security+
Security+ covers core cybersecurity principles. It explains threats and vulnerabilities clearly. Network security fundamentals receive strong focus. Risk management concepts are included. This certification suits beginners entering security roles.
Key focus areas:
-
Threat identification
-
Risk mitigation strategies
-
Basic cryptography
-
Access control mechanisms
Security+ builds essential theoretical strength.
Intermediate Certifications
After fundamentals, specialized certifications help. These focus on defensive analysis skills.
2. CompTIA CySA+
CySA+ emphasizes threat detection skills. It focuses on log analysis. Behavioral monitoring concepts are included. Candidates learn incident response basics. This certification suits aspiring analysts.
3. EC-Council CEH
Certified Ethical Hacker teaches attacker techniques. Understanding attacker mindset improves defense quality. It covers penetration testing basics. Ethical hacking tools are introduced. Knowledge gained supports investigation accuracy.
Advanced Incident Response Certification
Specialized credentials deepen incident handling expertise.
4. GIAC GCIH
GCIH focuses directly on incident handling. It covers attack detection techniques. Candidates study exploitation methods. Forensics fundamentals are included. This certification strengthens response capabilities.
Certification Comparison Overview
| Certification | Level | Focus Area | Suitable For |
|---|---|---|---|
| Security+ | Entry | Security fundamentals | Beginners |
| CySA+ | Intermediate | Threat detection | SOC Analysts |
| CEH | Intermediate | Attacker techniques | Defensive analysts |
| GCIH | Advanced | Incident handling | Incident responders |
Choose certifications based on career stage. Budget also influences decisions. Begin with strong foundations first.
Certifications open valuable opportunities. They improve structured knowledge depth. However, practical exposure remains essential. Employers value applied problem solving. Combine certifications with lab practice. Continuous learning ensures long term growth. Strategic certification planning supports career advancement.
Hands-On Practice and Labs
Practical experience builds real confidence. Theory alone cannot ensure readiness. Incident response requires applied problem solving. Labs simulate realistic attack scenarios. Practice strengthens technical reflexes. Repeated exposure improves investigation speed. Mistakes during practice build learning. Safe environments encourage experimentation.
Why Hands-On Practice Matters
Security incidents are unpredictable. Real alerts contain noisy data. Practical labs teach filtering skills. Analysts learn to identify true threats. Exposure to simulated attacks builds familiarity. Confidence grows with repeated investigations.
Key benefits include:
-
Improved log analysis accuracy
-
Recognize abnormal patterns faster
-
Reduce false positive mistakes
-
-
Better decision making
-
Practice containment steps safely
-
Test response strategies
-
-
Stronger technical confidence
-
Navigate tools comfortably
-
Troubleshoot unexpected issues
-
Consistent lab work bridges knowledge gaps.
Building a Simple Home Lab
A home lab provides safe practice space. Virtual machines simulate enterprise systems. Controlled environments allow attack simulations.
Basic setup steps:
-
Install virtualization software
-
Create Windows virtual machine
-
Create Linux virtual machine
-
-
Generate security logs
-
Simulate failed login attempts
-
Create suspicious network traffic
-
-
Practice investigation steps
-
Analyze event logs carefully
-
Document findings clearly
-
Regular practice builds muscle memory.
Online Practice Platforms
Online labs provide guided exercises. They offer structured learning paths. Many platforms simulate real world attacks.
| Practice Type | Focus Area | Outcome |
|---|---|---|
| Log Analysis Labs | Alert investigation | Faster detection skills |
| Blue Team Challenges | Defensive response | Improved containment ability |
| Capture The Flag | Attack simulation | Better analytical thinking |
Guided labs improve structured learning. Self paced challenges test creativity.
Developing Investigation Discipline
Document every lab exercise. Write short incident summaries. Track mistakes and corrections. Review weak areas weekly. Practice under timed conditions. Build systematic investigation habits.
Hands-on labs transform theoretical knowledge. Practical repetition strengthens retention. Safe simulations reduce fear of failure. Continuous practice prepares you for real incidents.
Career Opportunities and Salary
Incident response professionals remain highly in demand. Cyber attacks increase across industries. Organizations require skilled defensive experts. Security teams expand every year. Demand grows faster than supply. Skilled responders gain strong job stability. Career progression becomes structured and rewarding.
Entry-Level Opportunities
Beginners often start in support roles. These roles build investigation exposure. Experience strengthens analytical thinking.
Common entry roles include:
-
SOC Analyst
-
Monitor security alerts
-
Escalate confirmed incidents
-
-
Junior Security Analyst
-
Review system logs
-
Assist senior investigators
-
-
Incident Response Trainee
-
Support containment activities
-
Document investigation findings
-
Entry level roles focus on monitoring. Learning occurs through supervised practice.
Mid-Level and Advanced Roles
Experience opens specialized opportunities. Professionals handle complex incidents independently.
Career progression may include:
-
Incident Response Specialist
-
Lead investigation processes
-
Coordinate containment strategies
-
-
Threat Analyst
-
Study attacker behavior patterns
-
Develop detection rules
-
-
Digital Forensics Analyst
-
Examine compromised systems
-
Preserve investigation evidence
-
Senior professionals may lead teams. Leadership responsibilities increase gradually.
Salary Expectations in India
Salary depends on experience and skills. Certifications also influence compensation.
| Experience Level | Typical Salary Range | Growth Potential |
|---|---|---|
| Entry-Level | ₹4–7 LPA | Skill based growth |
| Mid-Level | ₹8–15 LPA | Leadership roles |
| Senior-Level | ₹18 LPA and above | Strategic positions |
Global salaries are significantly higher. Multinational firms offer competitive packages.
Long-Term Growth Potential
Cybersecurity remains future proof. Incident response supports organizational resilience. Continuous learning increases earning capacity. Specialized expertise improves negotiation power. Experience builds professional credibility. Strong performance attracts better opportunities.
Incident response offers stable career growth. Demand ensures consistent hiring trends. Skill development directly impacts salary progression. Dedicated professionals achieve rewarding careers.
Final Thoughts
Becoming an Incident Response Specialist in 6 months is achievable with structured learning and consistent practice. Focus on networking, security fundamentals, SIEM tools, and hands-on labs. Certifications add credibility, but practical skills matter most.
Cybersecurity rewards curiosity and continuous learning. Stay updated with new attack techniques. Practice regularly. Build projects and document your work. With dedication and discipline, you can successfully start your career in incident response within six months.
Frequently Asked Questions
Can I become an Incident Response Specialist in 6 months?
Yes, with structured learning and daily practice. Consistency is essential.
Do I need a degree to become an Incident Response Specialist?
No, skills and certifications matter more than degrees.
What skills are required for an Incident Response Specialist?
Networking, log analysis, and analytical thinking are crucial.
Are certifications important for an Incident Response Specialist?
Not mandatory, but they improve credibility and shortlisting chances.
Is coding required to work as an Incident Response Specialist?
Basic scripting helps, but deep coding is unnecessary initially.
How many hours should an aspiring Incident Response Specialist study daily?
Two focused hours daily are generally sufficient.
Are home labs necessary to become an Incident Response Specialist?
Yes, labs build practical confidence and investigation skills.
Which tools should an Incident Response Specialist learn first?
Start with operating system logs and basic SIEM concepts.
What is the starting salary for an Incident Response Specialist in India?
Entry-level salaries usually range from ₹4–7 LPA.
Is the Incident Response Specialist role stressful?
It can be demanding, but structured processes reduce pressure.