Table of Contents
Cybersecurity careers are growing very fast today. Many students think IT degrees are required. That belief stops many talented learners. But the industry values skills more. You can Become a SOC Analyst Without a Technical Degree. Yes, it is truly possible now. Companies focus on practical knowledge. Determination matters more than background.
Many non-technical students feel confused initially. They do not know where to start. The roadmap may seem complicated. However, the process can be simple. With the right guidance, progress becomes easier. Step-by-step learning builds strong confidence. Certifications improve your job opportunities. Practical training makes you industry ready. This guide will show the clear path.
Enroll in Entri’s AI-Powered Cybersecurity course now!
What Is a SOC Analyst?
Security Operations Center Analyst
A SOC Analyst protects organizations from cyber threats in real time. The term SOC stands for Security Operations Center. This center is a dedicated facility for monitoring security events. Continuous surveillance helps reduce potential cyber damage. Active monitoring ensures quick detection of suspicious behavior. Rapid response minimizes business disruption and financial loss. Strong attention to detail is essential in this role. Constant vigilance helps maintain digital safety. Overall responsibility focuses on defending systems and networks.
Security Operations Center Environment
A Security Operations Center operates in a structured setting. Large screens display dashboards filled with alerts. Multiple monitoring tools run simultaneously throughout the shift. Rotational shifts ensure twenty four hour coverage. Collaboration between team members strengthens incident handling. Clear communication improves response accuracy. Standard procedures guide every investigation process. Escalation paths remain clearly documented for emergencies. Organized workflows support efficient threat management.
Core Purpose of the Role
The primary objective involves detecting potential cyber threats early. Early identification prevents large scale security breaches. Careful observation helps separate genuine threats from false alerts. Alert validation reduces unnecessary panic and workload. Accurate analysis ensures correct decision making. Proper documentation supports future investigations. Escalation procedures activate when threats become serious. Coordination with senior teams enhances response effectiveness. Commitment to security remains central to daily tasks.
Key Responsibilities
Core duties revolve around monitoring, investigation, and reporting. Security alerts require immediate review and prioritization. Log files provide detailed evidence of system activity. Abnormal patterns often indicate potential risks. Suspicious login attempts demand deeper inspection. Malware indicators require rapid assessment. Confirmed threats must follow predefined response steps. Incident reports document every significant action. Accurate records help strengthen future defenses.
-
Monitoring Activities
-
Review automated security alerts
-
Track unusual access attempts
-
Observe system behavior changes
-
-
Investigation Tasks
-
Analyze server and firewall logs
-
Identify abnormal data transfers
-
Verify threat authenticity
-
-
Reporting and Documentation
-
Prepare detailed incident summaries
-
Maintain structured security records
-
Update internal tracking systems
-
Each responsibility supports overall organizational security.
Types of Threats Observed
Various cyber threats appear daily across networks. Malware infections can disrupt system performance. Phishing emails attempt credential theft. Ransomware attacks encrypt critical business data. Unauthorized access attempts target confidential systems. Insider threats sometimes emerge from internal users. Distributed denial of service attacks affect availability. Data exfiltration incidents risk sensitive information exposure. Continuous monitoring reduces potential damage from these risks.
| Threat Type | Description | Risk Impact |
|---|---|---|
| Malware | Harmful software infiltration | Medium to High |
| Phishing | Fraudulent credential attacks | Medium |
| Ransomware | Data encryption for payment | High |
| Unauthorized Access | Illegal system entry attempts | High |
| DDoS | Service disruption attack | Medium to High |
Careful evaluation determines appropriate response actions.
Tools Supporting the Role
Effective monitoring depends on specialized security tools. SIEM platforms centralize logs from multiple sources. Firewalls regulate incoming and outgoing traffic. Intrusion detection systems generate threat alerts. Antivirus software scans files for malicious code. Log management systems assist in pattern recognition. Automated alerts speed up detection processes. Manual review ensures contextual accuracy. Tool integration enhances overall visibility.
| Tool Category | Main Purpose | Key Function |
|---|---|---|
| SIEM Systems | Log aggregation | Alert correlation |
| Firewalls | Network control | Traffic filtering |
| Intrusion Detection | Activity monitoring | Suspicious behavior alerts |
| Antivirus Tools | Malware prevention | File scanning |
Understanding tool functionality improves investigation efficiency.
Role Structure Within Teams
SOC teams usually follow a tiered structure. Entry level analysts handle initial alert review. Intermediate analysts manage deeper investigations. Senior analysts oversee complex incidents. Escalation flows follow structured hierarchy guidelines. Clear role distribution ensures balanced workload. Advanced expertise supports difficult threat cases. Team collaboration improves resolution speed. Structured levels strengthen operational efficiency.
-
Level One
-
Monitor alerts
-
Perform initial checks
-
Escalate verified incidents
-
-
Level Two
-
Conduct advanced investigations
-
Support containment actions
-
Analyze recurring threat patterns
-
-
Level Three
-
Lead major incident response
-
Perform threat hunting activities
-
Mentor junior team members
-
Defined levels maintain clarity in responsibilities.
Daily Workflow Overview
Every shift begins with reviewing pending alerts. Prioritization depends on severity and risk level. High severity alerts receive immediate attention. Log analysis follows during investigations. Evidence collection supports accurate conclusions. Findings are documented carefully in tracking systems. Escalation occurs when required by protocol. Shift handovers include detailed summaries. Continuous monitoring continues until shift completion.
| Step | Activity | Objective |
|---|---|---|
| 1 | Review alerts | Identify priority issues |
| 2 | Analyze logs | Detect suspicious patterns |
| 3 | Investigate incidents | Confirm threat presence |
| 4 | Escalate cases | Ensure rapid response |
| 5 | Document actions | Maintain security records |
Consistent workflow improves operational stability.
Importance in Modern Organizations
Digital transformation increases cybersecurity risks significantly. Businesses rely heavily on interconnected systems. Data breaches cause financial and reputational harm. Regulatory compliance requires strong security monitoring. Proactive threat detection reduces long term damage. Continuous vigilance protects sensitive business information. Strong defense mechanisms maintain customer trust. Organized monitoring strengthens resilience against attacks. Critical infrastructure depends on reliable security operations.
A SOC Analyst plays a vital protective role. Continuous monitoring supports organizational safety. Structured processes guide effective incident management. Clear documentation improves long term defense strategies. Dedicated security teams form the backbone of cyber resilience.
Enroll in Entri’s AI-Powered Cybersecurity course now!
Do You Need a Technical Degree?
Many students believe a technical degree is mandatory for cybersecurity roles. This belief often discourages capable learners from applying. In reality, employers focus more on skills than degrees. Practical knowledge usually outweighs formal academic background. Demonstrated ability matters more than theoretical study alone. Strong fundamentals can be learned outside college classrooms. Structured self learning creates real industry readiness. Determination often bridges academic gaps effectively. A technical degree can help, but remains optional.
Industry Perspective on Degrees
Modern companies prioritize competence over academic labels. Hiring managers evaluate practical problem solving skills carefully. Interview rounds test understanding rather than memorization ability. Real world scenario questions reveal applied knowledge clearly. Certifications often carry strong industry recognition globally. Portfolio projects showcase capability more convincingly than transcripts. Recruiters assess adaptability and learning mindset seriously. Continuous learners stand out during recruitment processes. Skill based hiring trends are increasing worldwide.
What Employers Actually Look For
Organizations evaluate specific qualities during hiring stages. Clear understanding of core security concepts is essential. Basic networking awareness strengthens application credibility. Familiarity with common tools increases selection chances. Analytical thinking improves incident evaluation skills. Attention to detail reduces investigative mistakes significantly. Professional communication supports team collaboration effectively. Willingness to learn indicates long term growth potential. Consistency in learning builds employer confidence.
Below is a simplified comparison table:
| Hiring Factor | Importance Level | Reason |
|---|---|---|
| Practical Skills | High | Direct job relevance |
| Certifications | High | Validated knowledge proof |
| Degree Background | Medium | Academic foundation only |
| Projects | High | Demonstrated capability |
| Soft Skills | High | Team coordination support |
This table shows degree importance is moderate.
Alternative Learning Paths
Non technical students can choose multiple learning routes. Online courses provide structured foundational knowledge. Bootcamps offer focused practical training sessions. Self study through curated resources builds understanding steadily. Community forums support doubt clarification and networking. Practical labs enhance applied learning experience. Industry blogs improve awareness of trends. Webinars offer exposure to expert insights. Consistent practice builds confidence gradually.
Advantages of Skill Based Entry
Entering without a technical degree has benefits. Learners often develop strong self discipline. Independent research improves problem solving ability. Adaptability increases due to diverse backgrounds. Fresh perspectives enhance analytical thinking processes. Communication skills may be stronger among non technical graduates. Broader educational exposure supports creative solutions. Focused learning avoids unnecessary academic subjects. Career switchers usually demonstrate high motivation.
Challenges Without a Technical Degree
Absence of a technical degree may create hurdles. Initial concepts may seem unfamiliar. Technical jargon can feel overwhelming initially. Structured guidance becomes extremely important early. Time management is essential for self learners. Consistent practice requires personal commitment. Doubts must be clarified proactively. Confidence may fluctuate during early stages. Persistence becomes the key success factor.
Below is a challenge overview table:
| Challenge | Solution Approach | Outcome |
|---|---|---|
| Limited Technical Exposure | Start with basics | Strong foundation |
| Complex Terminology | Learn gradually | Improved understanding |
| Lack of Confidence | Practice regularly | Increased assurance |
| Interview Nervousness | Mock interviews | Better performance |
Proper strategy reduces these obstacles effectively.
Degree Versus Demonstrated Skill
Academic degrees provide structured theoretical learning. However, real world roles demand applied understanding. Demonstrated competence builds stronger employer trust. Hands on knowledge directly relates to job duties. Interview performance often determines final selection. Recruiters value candidates who explain concepts clearly. Practical demonstrations strengthen credibility significantly. Problem solving tests reveal true capability levels. Continuous improvement outweighs formal credentials.
Global Trend in Hiring Practices
Technology industries are shifting toward skill validation. Many global companies remove strict degree requirements. Competency based hiring models are expanding rapidly. Online certification platforms support accessible learning. Remote opportunities widen entry possibilities further. Open source communities encourage collaborative skill building. Professional networks highlight project based achievements. Portfolio driven evaluation is becoming standard practice. Academic exclusivity is gradually decreasing.
When a Technical Degree Helps
Formal education can provide structured academic depth. Complex theoretical topics may become easier to grasp. University labs offer guided experimentation opportunities. Peer learning improves conceptual discussions. Internship programs may be easier to access. Academic mentorship can accelerate foundational understanding. Research exposure strengthens analytical reasoning skills. Structured curriculum ensures comprehensive topic coverage. Still, these advantages remain supportive, not mandatory.
Final Clarification on Degree Requirement
A technical degree is not compulsory for entry. Skill development remains the primary success factor. Employers reward capability and practical readiness. Self learners can compete equally with graduates. Structured preparation bridges knowledge gaps effectively. Certifications validate expertise independently of degrees. Projects demonstrate seriousness toward career goals. Consistent effort produces measurable progress. Commitment ultimately determines professional success.
In simple terms, determination outweighs academic background. Focused learning opens doors in cybersecurity. Clear strategy transforms non technical beginnings into strong careers. Practical skills form the foundation of opportunity. Continuous improvement ensures long term growth.
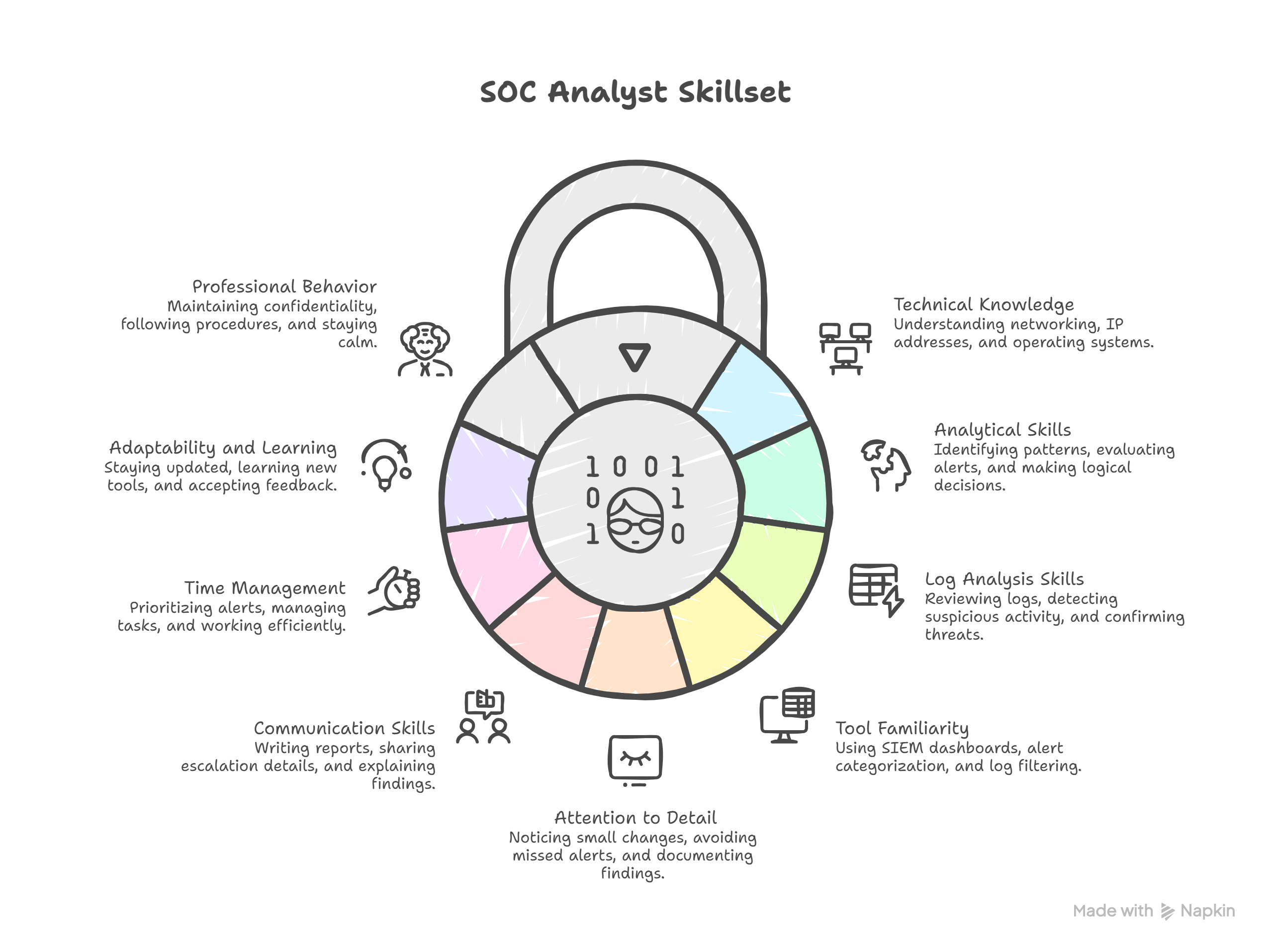
Skills Required to Become a SOC Analyst
Success in this role depends on strong core skills. Technical knowledge forms the foundation of performance. Analytical thinking strengthens investigation accuracy. Clear communication improves teamwork and reporting. Attention to detail reduces costly mistakes. Consistent learning keeps knowledge updated. Time management supports efficient task handling. Adaptability helps manage evolving threats. Balanced skill development ensures long term success.
Technical Knowledge Skills
Technical skills support daily monitoring activities. Basic networking knowledge is extremely important. Understanding IP addresses improves log interpretation. Knowledge of TCP and UDP supports traffic analysis. DNS awareness helps detect suspicious domains. Firewall basics assist in understanding blocked connections. Awareness of common protocols strengthens investigations. System fundamentals improve event understanding. Technical confidence increases investigative speed.
-
Networking Fundamentals
-
IP addressing concepts
-
Subnet basics
-
Protocol awareness
-
Packet flow understanding
-
-
System Basics
-
Windows processes knowledge
-
Linux command familiarity
-
File structure awareness
-
User permission basics
-
Below is a simple technical skill overview:
| Skill Area | Why Important | Practical Benefit |
|---|---|---|
| Networking | Understand traffic patterns | Detect anomalies |
| Operating Systems | Interpret system behavior | Identify suspicious activity |
| Protocol Knowledge | Analyze communication flows | Spot irregular traffic |
| Log Analysis | Review system records | Confirm threats |
Strong technical basics improve confidence significantly.
Analytical and Problem Solving Skills
Analytical thinking is essential in investigations. Alerts require careful evaluation before action. False positives must be identified correctly. Logical reasoning prevents incorrect escalation. Pattern recognition supports anomaly detection. Correlation skills link related security events. Critical thinking improves incident understanding. Structured analysis avoids rushed decisions. Patience enhances investigative accuracy.
-
Analytical Abilities
-
Identify unusual patterns
-
Compare normal versus abnormal behavior
-
Evaluate risk severity
-
Draw logical conclusions
-
Problem solving ensures efficient incident handling.
Attention to Detail
Small clues often reveal larger threats. Minor log changes may signal compromise. Overlooking details increases security risk. Careful observation strengthens detection accuracy. Precise documentation avoids confusion later. Thorough review reduces repeated incidents. Consistency improves long term reliability. Accuracy builds team trust. Focused attention enhances investigation quality.
Communication Skills
Clear communication supports effective teamwork. Reports must be concise and structured. Technical findings require simple explanations. Escalations demand accurate information sharing. Verbal clarity reduces misunderstandings. Written documentation ensures accountability. Professional tone strengthens credibility. Listening skills improve coordination. Strong communication supports smooth operations.
Below is a communication skills table:
| Communication Type | Purpose | Impact |
|---|---|---|
| Written Reports | Document incidents | Maintain records |
| Verbal Updates | Share urgent alerts | Quick response |
| Team Discussions | Coordinate actions | Efficient handling |
| Briefings | Shift handovers | Continuity maintained |
Effective communication strengthens overall efficiency.
Time Management Skills
Security alerts require prioritization skills. High severity cases demand immediate focus. Low risk alerts require documentation. Efficient scheduling prevents backlog accumulation. Organized workflow improves productivity. Multitasking ability supports shift management. Stress handling ensures steady performance. Quick decision making reduces delay. Balanced pacing avoids burnout.
-
Prioritization Skills
-
Assess severity quickly
-
Allocate time effectively
-
Avoid unnecessary delays
-
Strong time management improves performance quality.
Adaptability and Learning Mindset
Cyber threats evolve continuously. Learning mindset keeps knowledge current. Adaptability supports quick tool adjustments. Openness to feedback improves improvement speed. Curiosity encourages deeper research habits. Regular practice strengthens understanding. Self improvement ensures professional growth. Industry awareness increases readiness. Continuous learning supports long term relevance.
Tool Familiarity
Monitoring tools require confident handling. Dashboard interpretation improves response time. Alert filtering reduces unnecessary workload. Basic query writing strengthens analysis ability. Log search efficiency improves investigation speed. Understanding automation increases accuracy. Tool navigation skills save time. Familiarity enhances operational effectiveness. Practice builds technical comfort.
Below is a tools skill summary:
| Tool Skill | Purpose | Result |
|---|---|---|
| Dashboard Reading | Interpret alerts | Faster detection |
| Log Searching | Investigate incidents | Accurate findings |
| Alert Filtering | Remove noise | Efficient workflow |
| Basic Queries | Extract data | Better analysis |
Tool proficiency increases investigation quality.
Professional and Behavioral Skills
Professional conduct strengthens workplace reliability. Discipline ensures consistent monitoring standards. Ethical responsibility protects sensitive information. Confidentiality remains extremely important. Accountability improves team confidence. Positive attitude supports collaboration. Stress tolerance ensures stable performance. Respectful behavior enhances work environment. Professionalism builds long term reputation.
-
Behavioral Strengths
-
Integrity in reporting
-
Confidential handling of data
-
Responsible escalation
-
Calm under pressure
-
Balanced soft skills complement technical knowledge.
Summary of Essential Skills
Multiple skills combine for effective performance. Technical knowledge supports monitoring responsibilities. Analytical thinking improves threat identification. Communication ensures smooth coordination. Attention to detail reduces investigative errors. Time management strengthens workflow control. Adaptability ensures readiness for change. Tool familiarity increases operational efficiency. Professional behavior maintains organizational trust.
Below is a consolidated skills overview:
| Skill Category | Importance Level | Core Benefit |
|---|---|---|
| Technical Skills | High | Accurate analysis |
| Analytical Skills | High | Correct decisions |
| Communication | High | Effective teamwork |
| Time Management | Medium to High | Organized workflow |
| Professional Conduct | High | Trust and reliability |
Developing these skills creates strong capability. Balanced growth improves long term performance. Continuous improvement strengthens operational effectiveness. A well rounded skill set defines true competence.
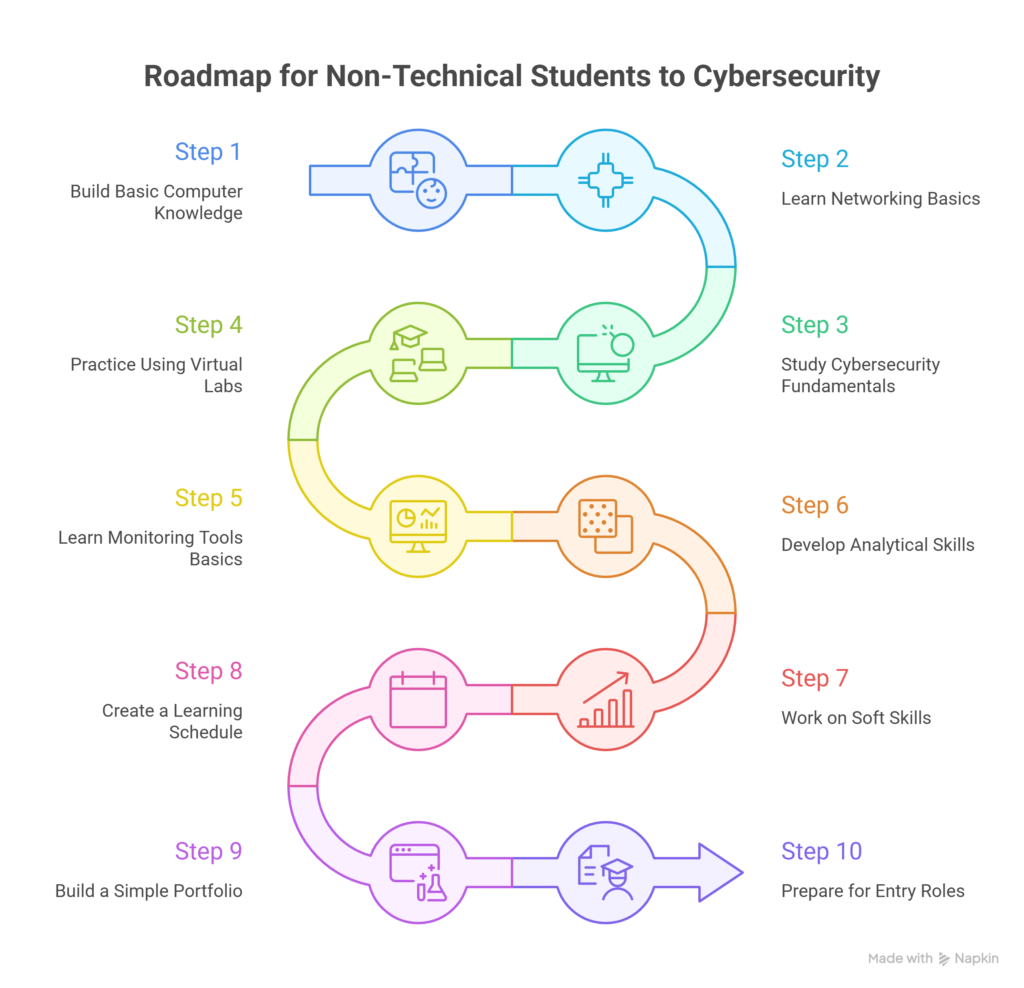
Step-by-Step Roadmap for Non-Technical Students
Starting without a technical background may feel challenging. However, a structured roadmap makes progress easier. Clear steps reduce confusion and overwhelm. Consistent effort builds confidence gradually. Practical exposure strengthens understanding over time. Focused learning prevents unnecessary distractions. Discipline ensures steady improvement. Patience supports long term growth. A systematic approach leads to career readiness.
Step 1: Build Basic Computer Knowledge
Begin with simple computer fundamentals. Understand how operating systems function. Learn about files and folders structure. Study basic hardware components and roles. Explore how applications interact with systems. Understand user accounts and permissions. Practice simple troubleshooting techniques. Gain comfort using both Windows and Linux. Strong basics create a stable foundation.
-
Core Fundamentals
-
File management basics
-
Process understanding
-
System settings navigation
-
Basic command line usage
-
Foundational knowledge supports advanced learning later.
Step 2: Learn Networking Basics
Networking knowledge is extremely important. Understand how devices communicate online. Learn what IP addresses represent. Study how data travels across networks. Understand common network protocols. Explore basic routing and switching concepts. Learn the purpose of firewalls. Understand ports and services basics. Networking clarity improves security awareness.
| Networking Concept | Why Important | Learning Outcome |
|---|---|---|
| IP Addressing | Identify devices | Better log analysis |
| Protocol Basics | Understand communication | Detect anomalies |
| Ports | Recognize services | Identify suspicious access |
| Firewalls | Control traffic | Understand filtering |
Clear networking understanding improves analysis ability.
Step 3: Study Cybersecurity Fundamentals
After networking, focus on security basics. Learn common types of cyber threats. Understand malware and phishing concepts. Study social engineering techniques. Learn about risk and vulnerability basics. Understand the importance of data protection. Explore concepts like encryption fundamentals. Study authentication and access control basics. Foundational security knowledge builds awareness.
-
Core Security Topics
-
Malware types
-
Phishing attacks
-
Password security
-
Access management
-
Solid fundamentals prepare learners for deeper topics.
Step 4: Practice Using Virtual Labs
Practical learning accelerates skill development. Set up a simple home lab. Install virtual machine software. Create practice environments safely. Explore system logs manually. Simulate small test scenarios. Practice analyzing network traffic. Learn basic troubleshooting methods. Hands on experience builds real confidence.
| Practice Activity | Purpose | Benefit |
|---|---|---|
| Virtual Machines | Safe experimentation | Practical understanding |
| Log Review | Identify patterns | Analytical growth |
| Traffic Monitoring | Observe network flow | Better interpretation |
| Scenario Practice | Simulate incidents | Improved response skills |
Consistent lab practice strengthens readiness.
Step 5: Learn Monitoring Tools Basics
Understanding security tools improves awareness. Study how monitoring dashboards function. Learn how alerts are generated. Understand severity levels classification. Practice reading sample logs. Explore basic search techniques. Understand filtering concepts in tools. Study how alerts are prioritized. Tool familiarity reduces learning curve later.
-
Tool Learning Focus
-
Alert categorization
-
Dashboard navigation
-
Basic query understanding
-
Log filtering techniques
-
Tool awareness improves technical comfort.
Step 6: Develop Analytical Skills
Investigation requires strong logical thinking. Practice identifying unusual patterns in data. Compare normal and abnormal behaviors. Solve small problem solving exercises daily. Analyze simple case studies carefully. Develop structured thinking habits. Avoid rushing through conclusions. Document findings clearly during practice. Analytical growth enhances decision making.
Step 7: Work on Soft Skills
Technical skills alone are insufficient. Communication skills improve teamwork efficiency. Practice writing short technical summaries. Explain concepts in simple language. Build confidence in discussions. Develop time management habits early. Practice handling pressure calmly. Improve listening during group tasks. Professional behavior strengthens workplace readiness.
| Soft Skill | Why Important | Result |
|---|---|---|
| Communication | Clear reporting | Better coordination |
| Time Management | Efficient workflow | Balanced productivity |
| Stress Handling | Stable performance | Reduced errors |
| Teamwork | Collaboration support | Faster resolution |
Balanced development improves overall performance.
Step 8: Create a Learning Schedule
Consistency is key for beginners. Create a weekly study plan. Allocate time for theory learning. Reserve hours for practical labs. Track progress regularly. Set small achievable milestones. Review previous topics frequently. Adjust schedule when needed. Discipline ensures steady improvement.
Step 9: Build a Simple Portfolio
Document practice activities carefully. Maintain notes of lab exercises. Create small project summaries. Highlight key learning outcomes. Organize documentation neatly. Showcase structured growth. Demonstrate consistent effort clearly. Keep records updated regularly. Portfolio evidence builds confidence.
Step 10: Prepare for Entry Opportunities
Once basics are clear, prepare professionally. Create a structured resume carefully. Highlight practical exposure clearly. Mention completed courses or certifications. Practice answering technical questions. Participate in mock interviews. Research common interview scenarios. Build confidence through repetition. Stay patient during application stages.
Roadmap Summary
Progress requires step by step discipline. Begin with computer fundamentals first. Move gradually into networking knowledge. Study security concepts after basics. Practice regularly in safe environments. Develop analytical and soft skills equally. Maintain a structured learning schedule. Document progress for clarity. Continuous effort ensures readiness.
| Roadmap Stage | Primary Focus | Outcome |
|---|---|---|
| Foundation | Computer basics | Strong base |
| Networking | Communication concepts | Technical clarity |
| Security | Threat understanding | Awareness growth |
| Practice | Hands on labs | Confidence building |
| Preparation | Resume and interviews | Career readiness |
A structured roadmap simplifies complex goals. Consistency transforms non technical beginnings into professional capability. Steady progress creates long term confidence. Focused effort builds meaningful expertise. Patience and discipline guide the journey forward.
Enroll in Entri’s AI-Powered Cybersecurity course now!
Frequently Asked Questions
Can I really become a SOC Analyst without a technical degree?
Yes, you absolutely can. Many companies prioritize skills over formal education. If you build strong fundamentals in networking and cybersecurity, you can compete confidently. Certifications and hands-on practice increase your credibility. Consistent effort and practical exposure matter more than your academic background.
How long does it take to prepare for a SOC Analyst role?
Preparation time depends on your learning pace and dedication. With focused daily study, beginners can build basic readiness in six to nine months. Consistency is more important than speed. Practical lab work accelerates understanding significantly. Structured learning makes the journey smoother and clearer.
Which certification should I start with as a beginner?
Beginners should start with foundational certifications like CompTIA Security+ or Network+. These certifications cover essential concepts in simple and structured ways. They validate your basic security knowledge. Employers recognize them globally. Starting with fundamentals builds confidence for advanced certifications later.
Do I need coding skills to become a SOC Analyst?
Advanced coding is not mandatory for entry-level roles. Basic scripting knowledge can be helpful but is not required initially. Most beginner roles focus on monitoring and log analysis. Strong analytical thinking is more important. You can gradually learn scripting as you grow.
Is the SOC Analyst role stressful?
The role can involve pressure during active incidents. However, structured processes guide investigations clearly. Team collaboration reduces individual stress. With experience, handling alerts becomes easier. Strong time management and calm decision-making help maintain balance.