Table of Contents
Cyber security offers strong career stability globally. Demand continues growing across multiple industries. Opportunities exist for both technical and nontechnical roles. Career paths support steady professional advancement. Skills development improves job security significantly. Certifications validate practical and theoretical knowledge. Early learning creates faster career growth opportunities.
Introduction: Why Cyber Security Is Evolving Rapidly
Cyber security is changing very quickly today. Technology is growing faster than ever before. Businesses depend heavily on digital systems. More systems mean more security risks. Every online activity creates possible threats.
Security methods must change with technology.
Companies now use cloud and online platforms daily. Employees work from different locations and devices.
Data moves constantly across networks. This makes protection more difficult. Old security methods cannot handle modern risks. New approaches are now necessary.
Cyber attackers are becoming smarter each year. They use better tools and planned strategies. Many attacks are financially motivated. This increases the number of cyber crimes. Defenders must improve faster than attackers.
Rules and data protection laws are also increasing. Organizations must follow strict security guidelines. Failure can lead to heavy penalties. Security has become a business priority.
Why Cyber Security Is Changing So Fast
- Technology adoption is increasing rapidly.
- Online data usage grows every day.
- Remote work expands security gaps.
- Attack methods change frequently.
- Digital systems are highly connected.
- Businesses demand stronger protection.
These reasons drive the fast evolution of cyber security. Professionals must stay updated to remain secure.
Key Cyber Security Trends in 2026
Cyber security is transforming due to advanced digital environments. Organizations face complex threats across platforms and devices. Security strategies now focus on prediction, prevention, and automation. The following trends define modern cyber defense approaches.
1. AI-Powered Threat Detection
Artificial intelligence is reshaping cyber security operations. Traditional systems cannot analyze massive data volumes. AI helps detect threats faster and accurately. It identifies abnormal behavior within networks.
Why AI-Based Detection Is Growing
- Cyber attacks generate huge data logs.
- Manual monitoring is time-consuming and inefficient.
- Threat patterns change continuously.
- Real-time response is now critical.
How AI Improves Security
- Monitors user behavior patterns continuously.
- Detects anomalies automatically.
- Reduces false security alerts.
- Predicts potential attack paths.
Key Applications
- Malware detection using behavioral analysis.
- Phishing identification through content scanning.
- Network intrusion detection systems.
- Endpoint activity monitoring.
Benefits for Organizations
- Faster threat response time.
- Improved detection accuracy.
- Lower operational workload.
- Enhanced decision-making support.
AI strengthens security teams rather than replacing them. Human expertise remains essential for final decisions.
2. Zero Trust Architecture
Zero Trust is a modern security framework. It follows the principle “never trust, always verify.” No user or device is trusted automatically.
Why Traditional Security Fails
- Network boundaries no longer exist.
- Cloud access bypasses internal firewalls.
- Remote work increases identity risks.
- Credentials are frequent attack targets.
Core Zero Trust Principles
- Continuous identity verification.
- Least-privilege access enforcement.
- Device health validation.
- Micro-segmentation of networks.
Zero Trust Components
- Identity and access management.
- Multi-factor authentication.
- Endpoint security checks.
- Continuous session monitoring.
Business Advantages
- Reduces insider threat risks.
- Limits lateral movement of attackers.
- Improves visibility across systems.
- Supports hybrid and cloud environments.
Zero Trust shifts focus from networks to identities. It becomes foundational for modern security strategies.
3. Cloud & IoT Security
Cloud and IoT adoption is increasing rapidly. Organizations rely on connected environments daily. This connectivity creates larger attack surfaces.
Cloud Security Challenges
- Misconfigured storage services.
- Insecure APIs and integrations.
- Shared responsibility misunderstandings.
- Limited visibility across multi-cloud environments.
IoT Security Challenges
- Weak device authentication mechanisms.
- Limited firmware updates.
- Hardcoded credentials.
- Poor encryption standards.
Key Security Measures
- Strong identity management systems.
- Continuous configuration monitoring.
- Network segmentation for devices.
- Secure firmware updates.
Cloud and IoT Protection Areas
| Area | Security Focus |
|---|---|
| Cloud Infrastructure | Access control and encryption |
| Applications | Secure APIs and monitoring |
| IoT Devices | Authentication and updates |
| Data Storage | Encryption and backup |
| Network | Segmentation and traffic analysis |
Why This Trend Matters
- Cloud workloads hold sensitive data.
- IoT devices operate in critical environments.
- Attacks can disrupt operations severely.
Security must scale with cloud and IoT growth.
4. Ransomware Evolution
Ransomware remains one of the top threats. Attack techniques have evolved significantly. Modern ransomware focuses on extortion models.
How Ransomware Has Changed
- Data theft occurs before encryption.
- Attackers threaten public data leaks.
- Double and triple extortion methods appear.
- Automated ransomware kits increase attacks.
Common Attack Entry Points
- Phishing emails.
- Compromised credentials.
- Unpatched vulnerabilities.
- Remote desktop exposure.
Modern Ransomware Characteristics
- Targets backups intentionally.
- Uses encryption-resistant techniques.
- Exploits trusted system tools.
- Operates through organized criminal groups.
Defensive Strategies
- Regular offline backups.
- Network segmentation.
- Email security filtering.
- Endpoint detection tools.
Organizational Impact
- Financial losses increase significantly.
- Business downtime becomes longer.
- Reputation damage affects customer trust.
Ransomware defense requires prevention and recovery planning.
5. Cyber Security Automation
Automation is becoming essential for security operations. Security teams face talent shortages globally. Threat volumes exceed manual handling capacity.
What Is Security Automation
Security automation uses predefined response actions. It reduces repetitive manual security tasks. It integrates tools for faster decision making.
Common Automated Functions
- Log collection and analysis.
- Alert prioritization.
- Threat intelligence correlation.
- Incident response execution.
SOAR Platforms
SOAR stands for Security Orchestration Automation Response. These platforms connect multiple security tools. They enable rule-based automated actions.
Automation Benefits
- Faster incident response times.
- Reduced human error.
- Improved analyst productivity.
- Better resource utilization.
Tasks Best Suited for Automation
| Task | Automation Benefit |
|---|---|
| Alert Triage | Reduces false positives |
| Malware Analysis | Faster detection |
| Incident Reporting | Standardized documentation |
| Threat Blocking | Immediate containment |
| Compliance Audits | Consistent evidence collection |
Automation supports analysts, not replaces them. Strategic thinking remains human-driven.
How These Trends Work Together
Modern cyber security is interconnected. Each trend supports the others.
- AI improves automation accuracy.
- Zero Trust strengthens identity security.
- Cloud security expands protection coverage.
- Automation improves ransomware response.
- IoT security integrates with Zero Trust models.
Organizations require unified security frameworks. Isolated tools no longer provide sufficient protection.
Why Professionals Must Understand These Trends
Cyber security roles are becoming specialized. Employers expect knowledge of modern architectures. Legacy-only skills are no longer enough.
Understanding trends enables professionals to:
- Design stronger security systems.
- Respond faster to incidents.
- Reduce business risk exposure.
- Improve career growth potential.
Summary
Cyber security in 2026 focuses on intelligence and automation. Threat detection relies heavily on artificial intelligence. Trust-based models are replaced by Zero Trust frameworks. Cloud and IoT environments demand continuous monitoring. Ransomware attacks continue growing in complexity. Automation becomes critical for operational efficiency.
Professionals must adapt to these evolving trends. Staying updated ensures relevance in the security landscape.
Enroll in Entri’s AI-Powered Cybersecurity course now!
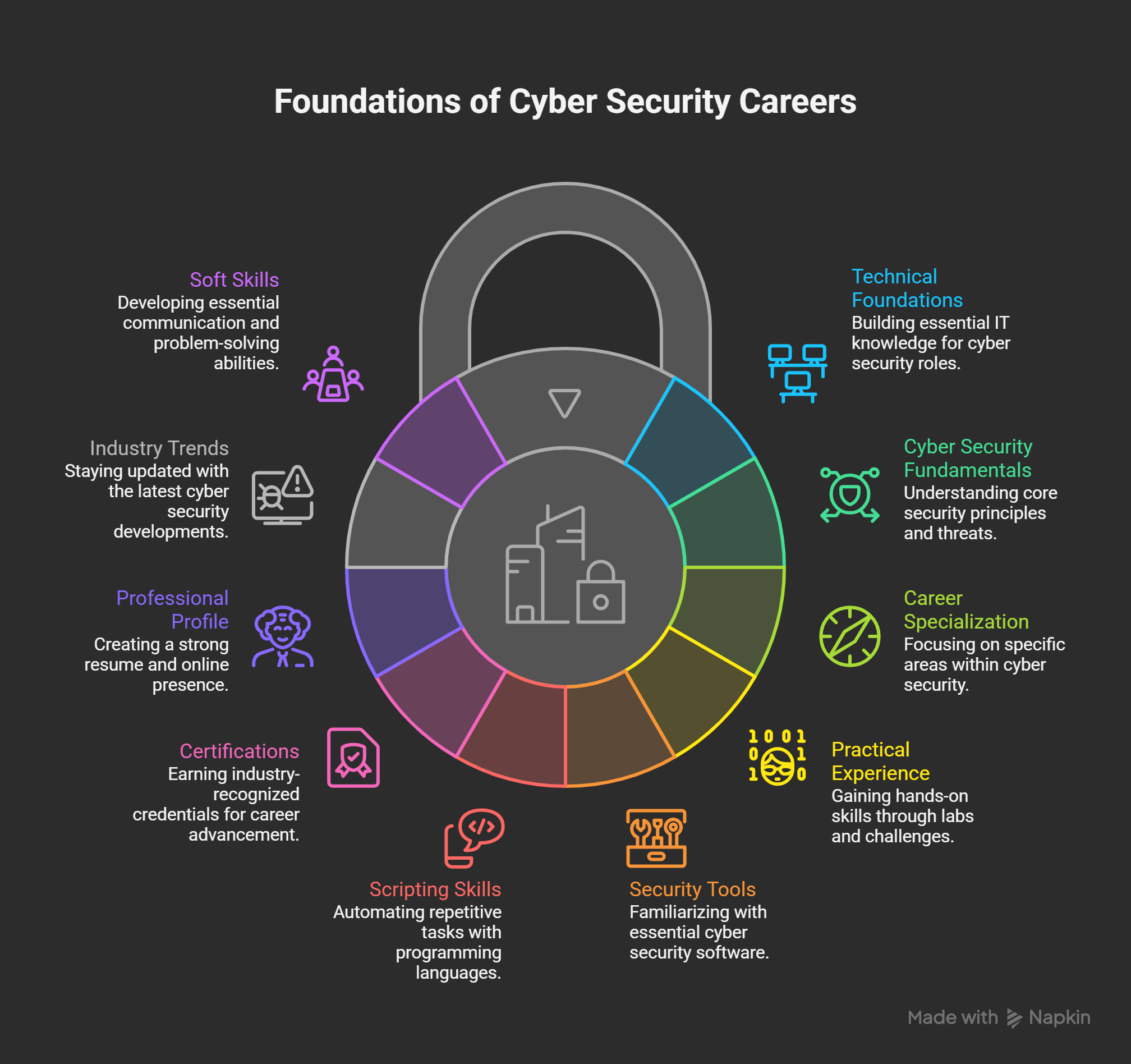
Skills Required in 2026
Cyber security professionals must adapt to rapid technology changes. Threat landscapes continue expanding across digital environments. Organizations seek professionals with modern and adaptable skillsets. Technical expertise alone is no longer sufficient. Balanced knowledge across domains is now essential.
1. Core Technical Skills
Strong technical foundations remain critically important. These skills support daily security operations.
a. Network Security Fundamentals
- Understanding TCP/IP and network protocols.
- Identifying suspicious network traffic patterns.
- Configuring firewalls and intrusion systems.
- Monitoring network performance and logs.
b. Operating System Security
- Securing Windows and Linux environments.
- Managing system permissions and policies.
- Detecting unauthorized system changes.
- Applying timely security patches.
2. Cloud Security Skills
Cloud adoption continues increasing worldwide. Security professionals must protect virtual environments effectively.
Key Cloud Security Areas
- Identity and access management.
- Secure cloud storage configurations.
- Cloud network segmentation.
- Encryption and key management.
Popular Cloud Platforms
| Platform | Security Skill Focus |
|---|---|
| AWS | IAM and monitoring |
| Microsoft Azure | Identity and compliance |
| Google Cloud | Data protection |
| Hybrid Cloud | Unified access control |
Understanding shared responsibility models is essential.
3. Threat Detection and Response Skills
Early threat detection reduces business impact. Security teams rely on monitoring and response expertise.
Important Capabilities
- Log analysis and correlation.
- Security Information Event Management usage.
- Endpoint detection tools operation.
- Incident response procedures execution.
Response Knowledge Areas
- Malware analysis basics.
- Attack containment methods.
- System recovery planning.
- Documentation and reporting processes.
4. Automation and Scripting Skills
Automation improves efficiency and accuracy. Manual security operations no longer scale.
Useful Automation Skills
- Python scripting fundamentals.
- PowerShell or Bash usage.
- API integration knowledge.
- Workflow automation design.
Benefits of Automation Skills
- Faster incident handling.
- Reduced repetitive workloads.
- Improved security consistency.
- Better operational visibility.
5. Identity and Access Management Skills
Identity is the new security perimeter. Access control prevents unauthorized system usage.
Key IAM Concepts
- Multi-factor authentication implementation.
- Role-based access control.
- Privileged access management.
- User lifecycle management.
IAM Tools Commonly Used
| Tool Category | Purpose |
|---|---|
| MFA Systems | Strong authentication |
| IAM Platforms | Access governance |
| PAM Tools | Privileged security |
| SSO Solutions | Centralized login |
Strong identity skills reduce breach risks significantly.
6. Governance, Risk, and Compliance Skills
Security must align with business regulations. Organizations face strict compliance requirements.
Key Knowledge Areas
- Risk assessment methodologies.
- Security policy development.
- Regulatory frameworks understanding.
- Audit preparation processes.
Common Frameworks
- ISO 27001 standards.
- NIST security framework.
- GDPR compliance principles.
- Industry-specific regulations.
These skills support long-term organizational security maturity.
7. Analytical and Problem-Solving Skills
Cyber security involves continuous investigation. Professionals analyze incidents under pressure.
Important Soft Skills
- Critical thinking ability.
- Attention to technical detail.
- Logical troubleshooting methods.
- Decision making during incidents.
Strong analysis prevents repeated security failures.
8. Communication and Collaboration Skills
Security teams work with multiple departments. Clear communication improves security awareness.
Communication Requirements
- Explaining risks to nontechnical users.
- Writing incident and audit reports.
- Coordinating with IT teams.
- Presenting findings to management.
Effective communication increases security adoption.
9. Continuous Learning Mindset
Cyber security evolves continuously. Skills become outdated quickly.
Learning Methods
- Industry certifications.
- Online security labs.
- Cyber range practice.
- Threat research reading.
Continuous learning ensures long-term career relevance.
Summary Table: Skills Required in 2026
| Skill Category | Importance |
|---|---|
| Technical Foundations | Core operations |
| Cloud Security | Infrastructure protection |
| Threat Response | Incident management |
| Automation | Efficiency improvement |
| Identity Security | Access control |
| Compliance | Risk management |
| Soft Skills | Team effectiveness |
| Continuous Learning | Career sustainability |
In Short
Cyber security roles demand diverse skillsets in 2026. Technical expertise must combine with analytical thinking. Cloud and automation knowledge remain essential. Identity and compliance skills support secure operations. Soft skills improve collaboration and communication. Continuous learning drives long-term career success.
Career Opportunities & Salary Outlook
Cyber security continues offering strong global career growth. Organizations face constant shortages of skilled professionals. Digital expansion increases demand across every industry. Security roles now support business continuity and trust. Career paths are diverse and highly scalable.
1. Entry-Level Career Opportunities
Entry-level roles build strong security foundations. These positions focus on monitoring and analysis.
Common Entry-Level Roles
- Security Operations Center analyst.
- Cyber security analyst.
- IT security support engineer.
- Vulnerability assessment analyst.
Key Responsibilities
- Monitoring security alerts and dashboards.
- Investigating suspicious system activities.
- Documenting incidents and responses.
- Supporting senior security teams.
Average Salary Range
| Region | Annual Salary |
|---|---|
| India | ₹4 – ₹8 LPA |
| Middle East | $40,000 – $70,000 |
| United States | $65,000 – $95,000 |
| Europe | €45,000 – €75,000 |
Entry roles provide exposure to real-world threats.
2. Mid-Level Career Opportunities
Mid-level professionals handle specialized security functions. These roles require hands-on technical expertise.
Popular Mid-Level Roles
- Security engineer.
- Cloud security specialist.
- Incident response analyst.
- Penetration testing consultant.
Typical Responsibilities
- Designing secure system architectures.
- Conducting vulnerability assessments.
- Leading incident response activities.
- Implementing advanced security controls.
Average Salary Range
| Region | Annual Salary |
|---|---|
| India | ₹10 – ₹20 LPA |
| Middle East | $70,000 – $120,000 |
| United States | $100,000 – $150,000 |
| Europe | €80,000 – €120,000 |
Experience significantly impacts salary progression.
3. Senior-Level Career Opportunities
Senior professionals manage enterprise security strategy. They focus on leadership and architecture decisions.
Senior-Level Roles
- Cyber security architect.
- Security operations manager.
- Risk and compliance manager.
- Chief information security officer.
Core Responsibilities
- Defining organizational security strategy.
- Managing security teams and budgets.
- Overseeing risk and compliance programs.
- Advising executive leadership.
Average Salary Range
| Region | Annual Salary |
|---|---|
| India | ₹25 – ₹60 LPA |
| Middle East | $130,000 – $220,000 |
| United States | $160,000 – $250,000 |
| Europe | €140,000 – €220,000 |
Leadership roles offer long-term stability.
4. High-Demand Specialized Roles
Certain cyber security roles command premium salaries. These roles require advanced expertise.
Top Specialized Positions
- Cloud security architect.
- DevSecOps engineer.
- Threat intelligence analyst.
- Digital forensics expert.
- Red team specialist.
Why These Roles Pay More
- Limited skilled professionals available.
- High impact on business security.
- Advanced technical requirements.
- Complex threat handling responsibilities.
5. Industry-Wise Career Opportunities
Cyber security jobs exist across all sectors.
Major Hiring Industries
- Banking and financial services.
- Healthcare and pharmaceuticals.
- Information technology services.
- Government and defense.
- E-commerce and retail.
- Energy and manufacturing.
Each industry requires specialized security controls.
6. Salary Growth Factors
Cyber security salaries vary widely. Several factors influence earning potential.
Key Salary Influencers
- Years of professional experience.
- Technical specialization area.
- Certifications and training.
- Organization size and location.
- Industry risk exposure.
Continuous skill upgrades increase compensation.
7. Certification Impact on Salary
Certifications improve employability and salary prospects.
High-Value Certifications
| Certification | Career Benefit |
|---|---|
| CEH | Ethical hacking roles |
| Security+ | Entry-level validation |
| CISSP | Leadership opportunities |
| CISM | Governance roles |
| Cloud Security Certs | Infrastructure specialization |
Certified professionals often earn higher packages.
8. Long-Term Career Outlook
Cyber security demand will continue rising. Digital dependency increases organizational risks. Automation cannot replace skilled professionals fully. Human decision-making remains essential.
Future Outlook Highlights
- Global talent shortages will persist.
- Salaries will grow steadily.
- Specialized roles will expand rapidly.
- Leadership positions will increase.
Summary Table: Career Growth Path
| Career Level | Roles | Salary Trend |
|---|---|---|
| Entry | SOC analyst | Moderate |
| Mid | Security engineer | High |
| Senior | Architect, manager | Very high |
| Specialist | Cloud, DevSecOps | Premium |
In Short
Cyber security offers strong long-term career potential. Opportunities exist across multiple experience levels. Salary growth remains higher than many IT fields. Specialization increases earning potential significantly. Continuous learning ensures sustained career success.
How to Prepare for Cyber Security Careers
Preparing for a cyber security career requires clear direction. The field demands both knowledge and practical skills. Early planning improves long-term success chances. A structured learning approach delivers better outcomes.
1. Build Strong Technical Foundations
Foundational knowledge supports advanced security learning. Beginners must understand basic IT concepts.
Core Areas to Learn
- Computer networking fundamentals.
- Operating system concepts.
- Basic system administration skills.
- Understanding how the internet works.
Why Foundations Matter
- Security builds upon core IT knowledge.
- Weak basics limit advanced understanding.
- Strong fundamentals improve troubleshooting ability.
2. Learn Cyber Security Fundamentals
Understanding security principles is essential. These concepts guide all defensive strategies.
Key Security Topics
- Confidentiality, integrity, and availability principles.
- Authentication and authorization methods.
- Common attack types.
- Basic encryption concepts.
Essential Knowledge Areas
- Malware types and behavior.
- Phishing and social engineering techniques.
- Network attack methods.
- Basic risk management concepts.
3. Choose a Career Specialization
Cyber security offers multiple career paths. Choosing a focus improves learning efficiency.
Popular Specializations
- Security operations and monitoring.
- Ethical hacking and penetration testing.
- Cloud security engineering.
- Governance, risk, and compliance.
- Digital forensics and incident response.
Specialization helps target relevant skills faster.
4. Gain Hands-On Practical Experience
Practical exposure strengthens theoretical knowledge. Employers prioritize hands-on abilities.
Ways to Gain Experience
- Virtual cyber security labs.
- Capture the Flag challenges.
- Home lab practice environments.
- Simulated attack and defense exercises.
Practical Skills Developed
- Tool usage confidence.
- Incident handling experience.
- Analytical thinking improvement.
- Real-world problem solving.
5. Learn Security Tools and Technologies
Modern security relies heavily on tools. Familiarity improves workplace readiness.
Important Tools to Practice
- SIEM platforms.
- Endpoint security tools.
- Vulnerability scanners.
- Network monitoring utilities.
Tool Skill Benefits
- Faster onboarding in organizations.
- Better understanding of enterprise environments.
- Improved detection and response capability.
6. Develop Scripting and Automation Skills
Automation skills improve efficiency significantly. They are highly valued by employers.
Recommended Skills
- Python scripting basics.
- Bash or PowerShell commands.
- API interaction concepts.
- Automation workflow understanding.
Automation reduces repetitive security tasks.
7. Earn Industry-Recognized Certifications
Certifications validate professional knowledge. They improve credibility and job opportunities.
Popular Beginner Certifications
| Certification | Purpose |
|---|---|
| CompTIA Security+ | Fundamental security knowledge |
| CEH | Ethical hacking skills |
| Network+ | Networking basics |
| Linux+ | System security foundation |
Certifications help resume shortlisting significantly.
8. Build a Strong Professional Profile
Employers review more than qualifications. A visible professional presence adds value.
Profile Development Steps
- Create a structured resume.
- Document hands-on projects.
- Maintain a professional online profile.
- Participate in security discussions.
Portfolio Examples
- Vulnerability assessment reports.
- Lab screenshots and documentation.
- Incident response simulations.
9. Stay Updated with Industry Trends
Cyber threats evolve continuously. Learning must never stop.
Effective Learning Methods
- Follow cyber security news platforms.
- Read threat research reports.
- Attend webinars and conferences.
- Join cyber security communities.
Continuous learning maintains professional relevance.
10. Improve Soft Skills and Mindset
Cyber security requires teamwork and communication. Technical skills alone are insufficient.
Important Soft Skills
- Clear written communication.
- Risk explanation to nontechnical users.
- Time management skills.
- Ethical decision making.
Strong soft skills accelerate career growth.
Preparation Roadmap Table
| Stage | Focus Area |
|---|---|
| Beginner | IT fundamentals |
| Intermediate | Security concepts |
| Advanced | Specialization |
| Professional | Tools and automation |
| Long-term | Continuous learning |
In Short
Cyber security careers require structured preparation. Foundations must be built before specialization. Hands-on practice increases employability. Certifications strengthen professional credibility. Automation and cloud skills add advantage. Consistent learning ensures long-term career success.
Enroll in Entri’s AI-Powered Cybersecurity course now!
Conclusion
Cyber security continues to evolve alongside rapid digital transformation. Organizations face increasing risks across systems and data environments. Understanding emerging trends helps professionals stay relevant. Modern roles demand updated technical and analytical skills. Career opportunities remain strong across industries worldwide. Continuous learning supports long-term professional stability. Prepared professionals can adapt confidently to future challenges.
Building a cyber security career requires consistent effort and focus. Structured learning improves skill development and confidence. Hands-on practice strengthens real-world problem-solving abilities. Certifications enhance credibility in competitive job markets. Staying updated ensures readiness for changing threats. With the right preparation, cyber security offers lasting growth and success.
Frequently Asked Questions
Is cyber security a good career choice in 2026?
Yes, cyber security remains one of the strongest career options in 2026 due to continuous digital expansion, increasing cyber attacks, and a global shortage of skilled professionals. Organizations across banking, healthcare, IT, government, and e-commerce require dedicated security teams to protect sensitive systems and data. As technology adoption increases, the need for cyber security experts grows steadily, ensuring long-term job stability and career growth.
Do I need a programming background to enter cyber security?
A programming background is helpful but not mandatory for beginners. Many entry-level roles focus on monitoring, analysis, and policy enforcement rather than coding. However, learning basic scripting languages like Python or PowerShell improves efficiency, automation skills, and career advancement opportunities. Over time, coding knowledge becomes an advantage rather than a requirement.
Which cyber security role is best for beginners?
Beginners commonly start with roles such as SOC Analyst, Cyber Security Analyst, or Security Support Engineer. These positions focus on alert monitoring, log analysis, and incident documentation. They provide exposure to real threats and enterprise tools, making them ideal starting points before moving into advanced or specialized roles.
How long does it take to become cyber security professional?
The timeline depends on learning consistency and background. With structured training, foundational skills can be developed within six to twelve months. Achieving job readiness may take additional practice through labs, certifications, and internships. Continuous learning remains essential even after securing employment.
What certifications are most valuable for cyber security careers?
Popular certifications include CompTIA Security+, CEH, CISSP, CISM, and cloud security certifications from AWS or Azure. Entry-level certifications help beginners understand fundamentals, while advanced certifications support leadership and specialization roles. Choosing certifications based on career goals delivers better results.
Can non-IT graduates build a career in cyber security?
Yes, many professionals transition into cyber security from non-IT backgrounds. With proper training, hands-on labs, and certification support, non-technical learners can acquire required skills. Basic IT concepts must be learned first, but strong analytical thinking and dedication can bridge the gap effectively.
What skills do employers look for most in 2026?
Employers prioritize cloud security knowledge, threat detection skills, identity management expertise, automation understanding, and incident response capabilities. Soft skills such as communication, documentation, and problem-solving are equally important. Professionals with adaptable skillsets stand out in recruitment processes.
Is cyber security stressful as a career?
Cyber security can be demanding, especially during active incidents or attacks. However, structured teams, automation tools, and defined response processes help manage pressure. Many professionals find the work rewarding due to its problem-solving nature and high impact on organizational safety.
What is the salary growth potential in cyber security?
Cyber security offers faster salary growth compared to many IT fields. Entry-level salaries increase significantly within three to five years through specialization and certifications. Senior and niche roles such as cloud security architects or DevSecOps engineers command premium compensation globally.
How can I stay updated in cyber security long term?
Staying updated requires continuous learning through threat reports, certifications, security blogs, labs, webinars, and community participation. Technology and attack methods evolve rapidly, making lifelong learning essential. Professionals who regularly upgrade skills maintain long-term relevance and career stability.