Table of Contents
Technology plays an increasingly important role in modern healthcare, particularly in the storage of patient records, the management of hospital operations, and the delivery of efficient care. This raises the possibility of cyberattacks, despite the fact that it is convenient. The protection of private patient data and the continuity of treatment are two of the most important goals of healthcare cybersecurity.
Join Entri’s Hospital Administration Course
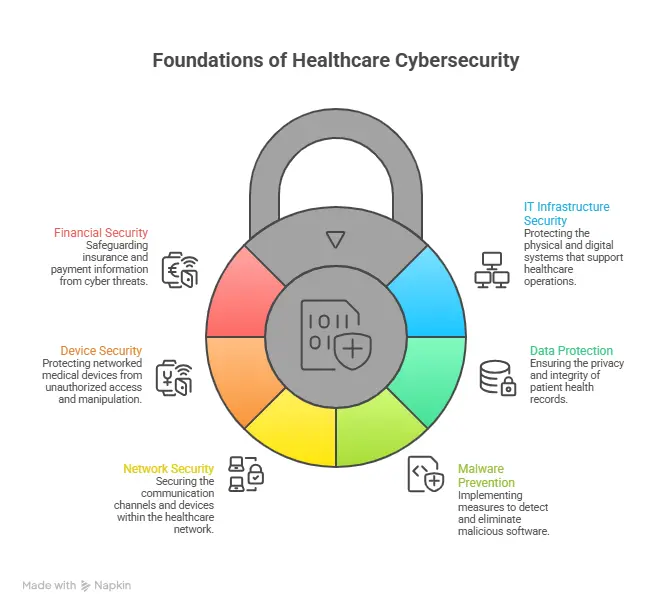
What Is Cybersecurity in Healthcare?
Protecting electronic health records, systems, and devices from intrusion, malicious software, or other cyber threats is what cybersecurity in healthcare is all about.
Methods like encryption, firewalls, and secure software are part of this process, which aims to protect:
- Documentation pertaining to the health of patients
- Efficient healthcare administration
- Networked medical equipment
- Invoices and information about health plans
Its primary function is to protect the privacy, authenticity, and accessibility of patients’ medical records.
Why Is Cybersecurity Important in the Healthcare Industry?
Protecting healthcare IT infrastructure, data, and electronic health records from unauthorized access, malware, and other cyber threats is known as cybersecurity.
Taking precautions means securing things with things like encryption, firewalls, and safe software to prevent:
- Patient health records
- Healthcare facility management software
- Networked medical devices
- Details regarding insurance and payments
Its principal role is to ensure that patients’ medical records are accessible, private, and secure.
Common Cybersecurity Threats in Healthcare
There are specific cyber dangers that are present in the healthcare industry. Included in this list are some of the more common ones:
- An example of a ransomware assault is when hackers encrypt hospital networks and then demand a ransom in order to break the encryption.
- The purpose of phishing emails is to trick recipients into giving critical information, such as login passwords, by using deception.
- A data breach occurs when hackers obtain unauthorized access to electronic health records (EHRs).
- The term “insider threat” refers to personnel who may divulge sensitive information. This could happen either accidentally or intentionally.
- It is possible to disrupt operations by infecting software in hospitals with malicious software and viruses.
- There are vulnerabilities in the security of the Internet of Things. It is feasible to hack linked medical devices, such as monitors and pacemakers.
Each of these dangers, if not addressed immediately, has the potential to delay treatments, result in the loss of data, and even put people’s lives in jeopardy.
Role of Hospital Administration in Healthcare Cybersecurity
Hospital administrators are very important for making sure that all areas are safe online. Some of their duties are:
- Making rules about protection and making sure everyone follows them.
- Staff members are being taught to spot scams and other strange activities.
- Spending money on safe technology and software changes on a regular basis.
- Working together with IT teams to keep an eye on system weaknesses.
- Making backup and rescue plans for data in case of an emergency.
Administrators help keep the healthcare setting safe and trustworthy by promoting a culture of cybersecurity awareness.
Join Entri’s Hospital Administration Course
Future of Cybersecurity in the Healthcare Sector
Hacking into health care will likely be hard and good in the future. As AI, the cloud, and healthcare grow, it will be harder to keep data safe.
Here are some new trends:
- Threat detection built on AI to protect you in real time.
- Blockchain technology lets people share medical information without risk.
- Cutting-edge ways to protect patient info by encrypting it.
- Some countries and regions need stricter rules about the internet.
It will be easier for hospitals to handle new threats if they buy smart security systems that can adapt to new situations.
Conclusion
1: What is the primary role of a hospital administrator?
The deployment of cybersecurity measures is now an urgent must for firms in the healthcare industry in order for them to continue their respective activities. In order to ensure the safety of medical equipment, the continuity of operations, the security of patient information, and the assurance of the safety of medical equipment are all vital components of a highly secure healthcare system. Hospitals may be able to keep their commitment to providing treatment that is both safe and reliable by improving their digital defenses and increasing their awareness. This is because the current world is interconnected, which means that hospitals are able to continue their commitment.
Hospital Administration Course with Assured Career Growth
Hospital Administration Course by Entri App: Master essential healthcare management skills, gain certification, and secure top roles in leading hospitals
Join Now!Frequently Asked Questions
How do cyberattacks affect hospitals?
Cyberattacks can disrupt hospital operations, delay treatments, leak patient records, and lead to financial and legal issues.
How can hospitals protect against cyber threats?
By using secure systems, encrypting data, updating software, conducting staff training, and implementing strong cybersecurity policies.
Who is responsible for cybersecurity in hospitals?
Hospital administrators, IT teams, and all healthcare staff share responsibility for maintaining cybersecurity awareness and compliance.
Can small clinics also face cybersecurity risks?
Yes. Even small clinics store sensitive data and can be targeted by hackers if they have weak security systems.
Is patient data safe in digital health systems?
It can be safe if proper encryption, secure cloud systems, and updated cybersecurity practices are followed.
How does cybersecurity affect patient trust?
When patients know their information is safe, they have greater confidence in the healthcare provider’s integrity and reliability.
Are cybersecurity skills taught in hospital administration courses?
Yes. Modern hospital administration programs often include cybersecurity management and digital data protection as key modules.