Table of Contents
Introduction
In cybersecurity, skills are more important than certifications. Today, employers focus on what you can do rather than what degree you have got. As cyber threats continue to grow, businesses need specialists who can exhibit real problem-solving skills, not just theoretical knowledge. This is where a cybersecurity portfolio comes in – it acts as solid proof of your skills and abilities, showing recruiters your hands-on experience in detecting threats, studying structures and protective information.
A well-structured portfolio can highlight your technical strengths, creativity and capability to address real-world problems or challenges. By the end of this article, you will realize how to create a cybersecurity portfolio that really impresses recruiters and how it help you to stand out in the competitive job market.
Enroll in Entri’s AI-Powered Cybersecurity course now!
Why you need a Cybersecurity Portfolio
In today’s cybersecurity job market, having a degree or some certifications isn’t sufficient. Recruiters now focus more on what you can truly do than what you have studied. They want to see proof, no longer simply learn about it, that you can tackle real security challenges. That’s why having a cybersecurity portfolio is vital. This allows you to showcase your projects – which include ethical hacking labs, malware analysis reviews, or examples of incident response work.
For people changing careers, a portfolio is a great way to build credibility and exhibit that you have the practical skills needed for the role. It also allows you stand out from others who may have similar certifications however lack real-world examples. According to a report by CyberSeek, about 65% of hiring managers prefer candidates who can demonstrate hands-on projects. In quick, your portfolio is the excellent proof of your abilities – and your chance to get recognized.
Building a cybersecurity portfolio would possibly appear intimidating at the beginning, however through breaking it down into smaller steps, you could create something that honestly highlights your talents and capability. Let’s undergo every step in an easy and practical way.
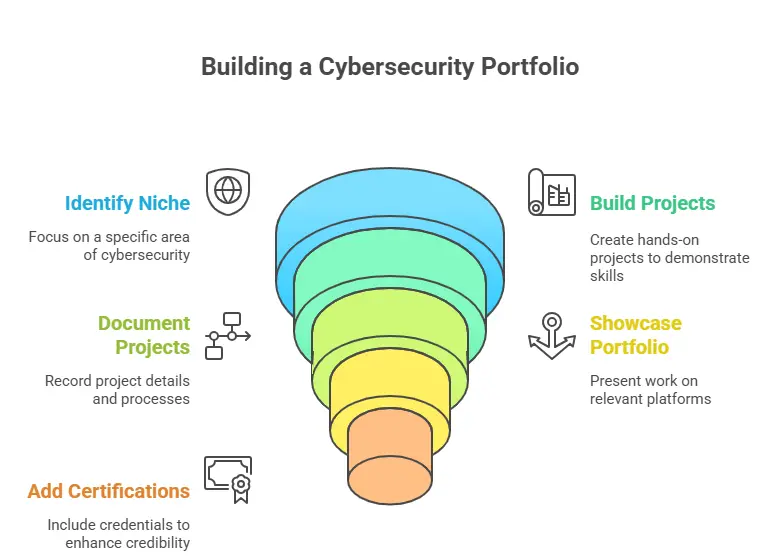
Step 1: Identify your Cybersecurity Niche
Before you start creating your portfolio, it’s essential to decide what field of cybersecurity you need to consciousness on. Cybersecurity is a large discipline with many paths, along with:
- Ethical Hacking/ Penetration Testing – finding and solving the protection vulnerabilities.
- SOC Analysis (Security Operations Center) – tracking networks for suspicious activities.
- Network Defense – putting in and dealing with secure community systems.
- Digital Forensics – investigating and analyzing the cyber incidents.
- GRC (Governance, Risk, and Compliance) – managing the safety regulations and dangers.
Why it matters: Focusing on a niche allows you create projects and skills that match your dream job. Recruiter prefer for portfolios that show a clear direction other than a mixture of unrelated work.
Step 2: Build Real-World Projects
Once you have chosen your interested field, start building projects that show your sensible talents. Hands-on experience will shows difference. Here are some project ideas:
- Ethical Hacking: To perform a vulnerability assessment on a demo website.
- SOC Analyst: Create simulated incident reaction reports or analyze fake alert logs.
- Network Security: Set up a firewall and record the way it protects network traffics.
- Digital Forensics: Analyze a sample malware record or a forensic disk photograph to hint an assault.
Use platforms like TryHackMe, Hack The Box, or Splunk’s free labs to practice safely. These platforms allow you to test your skills without legal risks.
Step 3: Document Everything
Doing projects is important—however displaying how you did them is even better. Documentation gives recruiters a clear view of your process and thought patterns. You can write brief reviews, create GitHub READMEs, or mini case studies. Keep your layout simple and consistent, as an example:
Objective → Tools Used → Process → Findings → Mitigation Steps
Example:
- Objective: Testing web app for vulnerabilities.
- Tools Used: Burp Suite, OWASP ZAP.
- Process: Performed computerized scans, then manual testing for SQL injection.
- Findings: Discovered susceptible login page.
- Mitigation Steps: Suggested parameterized queries and input validation.
Add screenshots or diagrams where feasible—they make your portfolio extra attractive and professional.
Step 4: Showcase on the Right Platforms
Your project need to be visible to the proper recruiters. Here’s where you could host and share your portfolio:
- GitHub: Upload scripts, configs, or reports.
- Personal Website or Blog: Write approximately your studying adventure and initiatives.
- LinkedIn “Featured” Section: Highlight top projects or certifications.
- Cybersecurity Portfolio Sites: Use Notion, GitBook, or a digital portfolio template to prepare your project well.
Add visuals—screenshots of dashboards, graphs, or redacted logs—to help recruiters quickly understand your project.
Step 5: Add Certifications & Learning Proof
Certifications and continuous learning display commitment to the field. While talents rely on most, having certifications can complement your portfolio. Include credentials like:
- CompTIA Security (for beginners)
- CEH (Certified Ethical Hacker)
- OSCP (Offensive Security Certified Professional)
- CISSP (for skilled experts)
Also mention your participation in Capture the Flag (CTF) challenges, bug bounty programs, or cybersecurity competitions. These show that you actively practice your skills in real-world scenarios.
Step 6: Tailor Portfolio for Job Applications
Finally, customize your portfolio for every job you applied.
- If you’re applying for a SOC analyst position, mention log evaluation and incident response initiatives. For penetration testing, focus on ethical hacking and vulnerability assessment works.
- Add a brief “About Me” section on the top of your portfolio. Share who you’re, your interests on cybersecurity field, and your career focus. This personal touch facilitates recruiters hook up with you on a human level.
Bonus: Mistakes to Avoid
Creating a cybersecurity portfolio can be interesting, however there are a few errors that may hurt your chances of impressing recruiters. Avoiding these simple mistakes will make your portfolio more stronger, more professional, and completely truthful. Let’s examine some of the most important mistakes and a way to fix them.
1. Copy-Pasting Code Without Explanation
One of the common mistakes is without a doubt copying someone else’s GitHub project or code and pasting it into your portfolio. Recruiters can easily find out this. They’re now not simply searching out results – they want to apprehend your thinking ability. If you use open-source tools or code snippets (that is completely nice), ensure to explain how you used them. Describe the problem you solved, what adjustments you made, and what you discovered. Showing your personal contact and understanding subjects far more than simply having “best” code.
2. Including Confidential or Sensitive Information
Never encompass actual organization data, client information, or anything that might disclose sensitive structures. Although you worked on a practical project, always redact or anonymize information earlier than including them for your portfolio. For example, update business enterprise names with placeholders like “Client A” or “Internal System.” This suggests which you respect privacy and observe ethical security practices – something every recruiter will admire.
3. Ignoring Readability and Structure
A portfolio that’s messy or hard to navigate can turn recruiters away, although the content material is great. Avoid dumping files and screenshots with out context. Instead, organize your portfolio with clear sections and steady formatting. Add quick introductions, label each project, and include a short summary of what every one illustrates. You also can use bullet points, visuals, and simple headings to make it easy to browse. Remember, a clean and readable format suggests professionalism and attention to detail— key trends in cybersecurity.
4. Not Updating Your Portfolio Regularly
Cybersecurity is a fast-moving area, and your portfolio should replicate your most latest skills and projects. Many candidates make the mistake of building their portfolio once and never touching it once more. Update your portfolio for every few months. Add new projects, certifications, or write approximately recent experiences. An up-to-date portfolio shows that you’re energetic, curious, and continuously improving.
Final Touches to Impress Recruiters (Tips Section)
Once your cybersecurity portfolio is complete, it’s time to polish it up and make it shine. These small however effective completing touches could make a great difference in how recruiters see you. Think of this step as including the final layer of professionalism that allows your portfolio stand out in recruiters mind.
1. Write a Clear and Friendly Introduction
Start your portfolio with a brief introduction that tells recruiters who you’re and what drives you. Keep it personal yet professional. Like, should share what inspired you get into cybersecurity career, and what kind of roles you’re seeking out. This helps recruiters quickly understand your desires, interest and goals before diving into your project.
2. Make It Visually Appealing
An easy and visually prepared layout is easier to read and more exciting to discover. Use consistent colors, fonts, and formatting throughout in your portfolio. Break up long textual content with bullet points, headings, and visuals including screenshots or community diagrams. If you’re building a website-primarily based portfolio, use an easy template that loads quickly and appears professional touch on both PC and mobile devices.
3. Add Contact Information and Links
Make it clear for recruiters to reach you. Add a professional mail ID, your LinkedIn profile, and links for your GitHub or personal website. If you have got different profiles like Hack The Box, TryHackMe, or a weblog, include them too. Just ensure all hyperlinks are active and result in up-to-date content.
4. Include Short Project Summaries
Recruiters don’t always have time to check lengthy reports. Add brief summaries or highlights for each projects that briefly explain what the project is, what tools you used, and what you completed.
For example: Performed a vulnerability scan on a demo web app the usage of OWASP ZAP and Burp Suite. Identified 3 essential issues and proposed mitigation steps. This enables recruiters get the main concept quickly while displaying your technical and communication skills.
5. Ask for Feedback and Keep Improving
Before sending your portfolio to recruiters, share it with mentors, friends, or online cybersecurity communities. Ask for honest feedback – sometimes small suggestions can make big improvements. Keep updating your portfolio as you learn new tools, complete more projects, or earn certifications.
Enroll in Entri’s AI-Powered Cybersecurity course now!
Conclusion
Creating a cybersecurity portfolio is one of the best approaches to exhibit your skills and stand out within the competitive job market. In today’s enterprise, recruiters care approximately what you may do extra than your degrees or certifications. A well-structured portfolio reflects your actual problem-solving skills, your understanding of tools and strategies, and your dedication to gaining knowledge of new technology.
Your portfolio is more than just a collection of projects – it highlights your individual contributions as a cybersecurity professional. Whether it’s ethical hacking, network security, SOC assessment or digital forensics, whatever project you’re involved in will help recruiters see your precise strengths. Remember to document your work simply, keep your design perfect, and update it often with new projects and achievements.
By following the steps in this guide, you can create a portfolio that showcases not only your technical skills, however additionally reflects your passion and professionalism. Be consistent and let your portfolio grow like your career. With the proper effort, your cybersecurity portfolio can be the key that opens the door to exciting opportunities in the field.
Frequently Asked Questions
What is a cybersecurity portfolio, and why do I need one?
A cybersecurity portfolio is a collection of your hands-on projects, reports, and achievements that demonstrate your technical skills and problem-solving ability. It helps recruiters see your real-world experience, not just your qualifications. In a field where skills matter most, a strong portfolio can set you apart from others who only list certifications.
What should I include in my cybersecurity portfolio?
Include real-world projects, documentation, and evidence of your skills. Examples can be ethical hacking reports, SOC analysis logs, firewall configurations, or digital forensic investigations. You can also add certifications, participation in CTF challenges, and blog posts explaining your work.
How many projects should I include in my portfolio?
Quality matters more than quantity. Start with 3 to 5 strong projects that highlight your core strengths and the areas you want to work in. Each project should clearly show what you did, what tools you used, and what you learned from the experience.
Do I need coding skills to build a cybersecurity portfolio?
Not always. While basic scripting or coding knowledge can be helpful, many cybersecurity roles—like SOC analysis, GRC, or forensics—focus more on investigation, documentation, and tool usage. However, learning a bit of Python, Bash, or PowerShell can make your portfolio more versatile.
Can beginners create a cybersecurity portfolio without job experience?
Absolutely! You don’t need professional experience to start. Use free learning platforms like TryHackMe, Hack The Box, Blue Team Labs Online, or RangeForce to complete labs and document your progress. Showing your learning journey and self-initiative impresses recruiters just as much as formal experience.
How do I present my portfolio to recruiters?
You can host your portfolio on platforms like GitHub, Notion, or your own personal website. Share a clean link in your resume and LinkedIn profile. Make sure your portfolio is easy to navigate, visually clear, and free from broken links or outdated content.
How often should I update my cybersecurity portfolio?
Update your portfolio every few months or whenever you complete a new project, earn a certification, or learn a new tool. Cybersecurity evolves quickly, so keeping your portfolio current shows that you stay active and engaged in the field.
What are common mistakes to avoid when creating a cybersecurity portfolio?
Avoid copying code without explanation, sharing confidential data, or neglecting documentation. Don’t let your portfolio become outdated or cluttered. Keep it organized, simple to read, and focused on projects that match your career goals. Always add personal insights about what you learned and how you solved problems—it shows your genuine understanding.