Table of Contents
Comprehending the methods to maintain your computer’s security online is becoming essential. Organizations must employ individuals capable of penetrating and securing their systems due to the increasing sophistication of hackers. In the realm of cybersecurity, people may be categorized into two primary groups: the prudent and vigilant, and the audacious and proactive in their self-defense. Although both are essential, separate ideas, methodologies, and competencies are required for each. Comprehending the differences between the two professions may aid you in ascertaining if a career in cybersecurity is the appropriate option for you.
Enroll in Entri’s AI-Powered Cybersecurity course now!
What Is Offensive Cybersecurity (Red Team)?
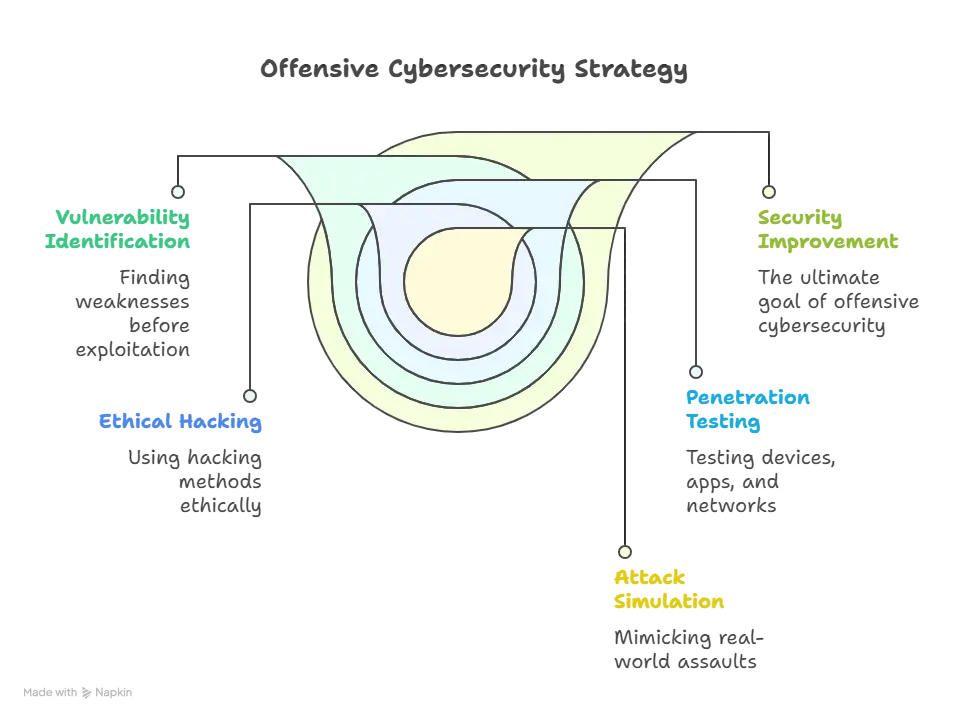
Offensive cybersecurity, sometimes referred to as the Red Team, focuses on adopting a hacker’s mindset. Red team personnel use a proactive strategy by mimicking real-world assaults, rather than awaiting hackers’ actions. Their objective is to identify vulnerabilities prior to their exploitation by malevolent entities. Important duties include:
- Conducting penetration tests on devices, apps, and networks
- Finding weaknesses via the use of ethical hacking methods
- Impersonating social engineering, malware, or phishing assaults
- Taking use of weaknesses to illustrate the possible consequences of a breach
- Creating thorough reports with suggestions to improve security
You need creativity, curiosity, and problem-solving abilities to be successful on this road. To keep ahead of cybercriminals, red team members need to continuously master the newest hacking tools and methods, such as Kali Linux, Burp Suite, and Metasploit.
What Is Defensive Cybersecurity (Blue Team)?
Defender cybersecurity, sometimes known as the “Blue Team,” seeks to protect networks against assaults. The blue team strives to maintain systems secure, strong, and equipped to manage challenges in the real world. The red team, on the other hand, seeks to break into systems. Important duties include:
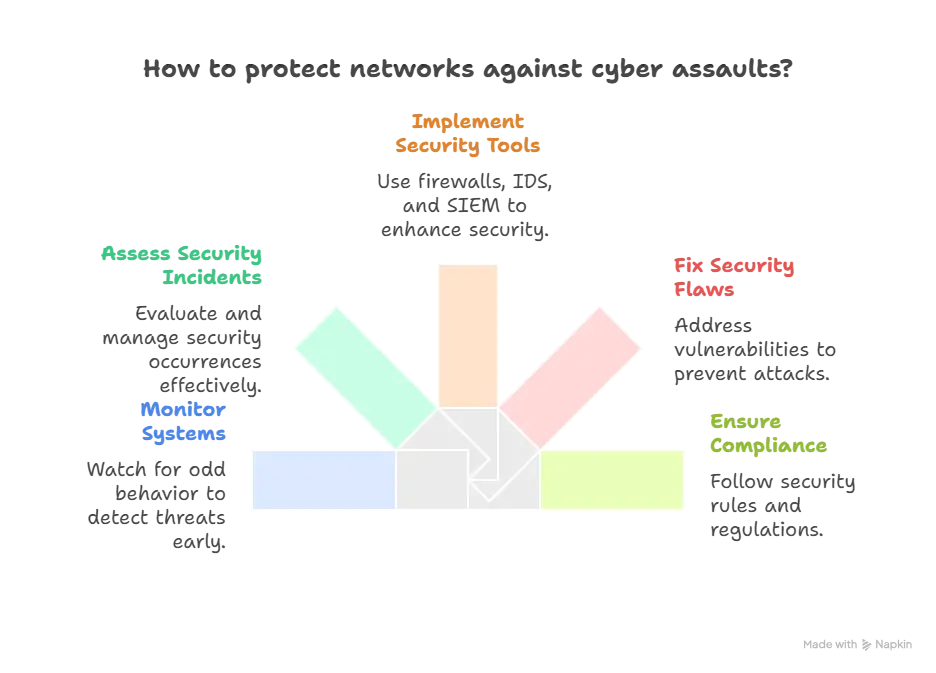
- Watching systems and networks for odd or harmful behavior
- Seeing security occurrences, assessing them, and taking care of them
- Putting together and running firewalls, intrusion detection systems (IDS), and security information and event management (SIEM)
- Fixing security flaws and figuring out how risky something is to stop an attack
- Make sure that safety rules and regulations are followed
Blue team members need to be brave and critical and pay attention to details since they are frequently the first people to respond to an assault. Splunk, Wireshark, Snort, and Endpoint Detection and Response (EDR) are some of the tools they utilize a lot.
How Do Offensive and Defensive Cybersecurity Differ?
Cybersecurity is like a war zone where defenders strive to block attackers from getting in without permission. After that, the offensive (red team) and defensive (blue team) responsibilities in cybersecurity are turned on. The blue team’s duty is to safeguard systems and deal with threats, whereas the red team’s objective is to find weaknesses by staging assaults. If you can tell the difference between the two, you’ll have a better notion of which method is ideal for you.
| Aspect | Offensive Cybersecurity (Red Team) | Defensive Cybersecurity (Blue Team) |
| Objective | Simulate attacks and exploit vulnerabilities | Protect systems and respond to attacks |
| Approach | Break into systems to find gaps | Build defenses to block attacks |
| Mindset | Think like a hacker | Think like a protector |
| Core Tasks | Penetration testing, ethical hacking, social engineering | Monitoring, incident response, risk management |
| Tools Used | Kali Linux, Metasploit, Burp Suite | Firewalls, SIEM tools, IDS/IPS, Wireshark |
| Outcome | Report showing security flaws | Stronger defense and minimized risk |
| Work Style | Creative, unpredictable, attacker-focused | Analytical, structured, defender-focused |
Which Cybersecurity Path Suits Your Personality and Skills?
The decision between defensive and offensive cybersecurity often boils down to your own preferences and areas of interest. Strong technical knowledge is necessary for both routes, but how you use your abilities will vary greatly.
Offensive Cybersecurity (Red Team): The Ethical Hacker
If you appreciate solving challenges, trying new things, and finding clever ways to get past rules, the red team could be the best choice for you. Offensive specialists need to think like attackers and utilize their imaginations to uncover flaws that other people may not see. People who prefer challenges, surprises, and “breaking things” to learn how they work could be well for this career. If you:
- Like taking things apart and finding out how they function.
- Be curious and love testing the limits.
- Do well when things are moving quickly and there is a lot of stress.
Defensive Cybersecurity (Blue Team): The Defender
The Defender: Defensive Cybersecurity (Blue Team) If you want things to be stable and are more detail-oriented, the blue team could be a good match for you. Digital protectors are defensive professionals who keep an eye on systems all the time, look for risks, and put precautions in place to avert damage. This plan includes being aware of and patient with threats and taking action to protect yourself. If you:
- Pay close attention to the little details.
- It’s better to build secure systems than to breach them.
- Like watching patterns, checking facts, and being safe before problems happen.
What Career Opportunities Are Available in Each Path?
There are great job possibilities in both offensive and defensive cybersecurity, and they both have a lot of room to develop. Your interests, talents, and preferred way of working will help you choose.
Careers in Offensive Cybersecurity (Red Team)
Professionals in offensive security work to find and use weaknesses to help businesses strengthen their defenses. Some common jobs are:
- Penetration Tester: Tests systems by pretending to be an attacker to uncover weak spots.
- Ethical hacker: An ethical hacker looks for weaknesses in apps, networks, and devices by testing them.
- Red Team Specialist: Does full-scale attack simulations, such as social engineering and network attacks.
- Exploit Developer: makes programs and tools to find weaknesses.
- Security Researcher: Looks into new risks and finds new ways to hack.
These jobs frequently need people who are good at solving problems, know how to code, and are creative.
Careers in Defensive Cybersecurity (Blue Team)
Defensive jobs are all about keeping systems safe and reacting to threats. Some of the most popular jobs are:
- Security analyst: A Security analyst looks at records, watches networks, and finds questionable activities.
- Incident Responder: Looks into security breaches and makes sure that recovery activities go well.
- Security Engineer: Makes and puts into action safe systems and processes.
- SOC (Security Operations Center) Analyst: Watches for alarms in real time and takes action when an attack could happen.
- Threat Intelligence Specialist: Looks at threats and tries to guess how they could strike.
People in these jobs usually need to be able to pay attention to details, analyze analytically, and handle risks before they happen.
Opportunities for further career growth
Both pathways provide opportunities for professional advancement to senior positions such as:
- Consultant for Cybersecurity
- Architect of security
- Chief Information Security Officer (CISO)
- Manager of Cybersecurity
Cybersecurity provides promising career opportunities, including strong demand, attractive compensation, and the opportunity to make a tangible difference in the world, regardless of whether you choose to specialize in offensive, defense, or a combination of both (purple team).
Enroll in Entri’s AI-Powered Cybersecurity course now!
Conclusion
You can choose between aggressive and defense hacking based on your skills, hobbies, and way of thinking. Offensive jobs (red team) are best for people who like to think like attackers, be clever, and solve problems. The best people for defense jobs (blue team) are those who pay attention to details, think critically, and want to keep systems safe. In purple team jobs, some people even use both skills. No matter what path you take, a job in cybersecurity will keep you learning, give you interesting tasks, and give you a lot of chances to succeed. If you love technology and keeping things safe online, this is a great job for you.
| Related Articles | |
| Entri Launched AI-Powered Cybersecurity Course | Cybersecurity Career Path |
| An Introduction to Cybersecurity Ethics | Top Cybersecurity Languages to Learn |
Frequently Asked Questions
Can I switch between offensive and defensive cybersecurity roles?
Yes! Many professionals start in one area and transition to the other as they gain experience or expand their skills.
What is a Purple Team?
A Purple Team combines skills from both offensive and defensive cybersecurity, helping organizations strengthen defenses while understanding attacker techniques.
Can beginners enter either path?
Absolutely. Many start in entry-level positions like SOC analyst (blue team) or junior penetration tester (red team) and grow into more advanced roles over time.
Do I need coding skills for these roles?
Yes. Red team roles usually require deeper coding knowledge for exploits, while blue team roles benefit from scripting for automation and monitoring.
Which path pays more?
Salaries depend on experience and location, but offensive roles like penetration testers often earn slightly higher pay due to high demand.