Table of Contents
These days, technology is everything. It facilitates our ability to communicate with loved ones, purchase online, bank while on the road, and get healthcare. Some chores are made simpler by these adjustments, but foes may now reach them faster. This explains why it appears like internet frauds, malware assaults, and data intrusions occur daily. Businesses need responsible hackers to address these concerns. Hacking must be done immediately. “Ethical hacking,” also referred to as “white-hat hacking,” is a technique for identifying and repairing vulnerabilities in computer networks, programs, and systems before hackers can take use of them to do damage. By improving security, moral hackers prevent fraud, preserve private data, and foster trust. Learning the fundamentals of ethical hacking is entertaining and fascinating. Another benefit may be stable defense employment.
Enhance your data science skills with us! Join our free demo today!
What Is Ethical Hacking, and Why Does It Matter?
Finding possible weaknesses in computer networks, software, and systems that might provide malevolent actors access without authorization is the aim of ethical hacking. Unlike criminal hackers, ethical hackers are always authorized to hack, never violate the law, and share their insights to improve or maintain systems. The importance of this is shown by the startlingly quick rise in cyberattack frequency. The following might happen in the case of a single data breach:
- They lost millions and millions of dollars.
- The credibility of businesses suffers.
- The company’s standing is deteriorating.
- problems with following the law and regulations.
As a result of their capacity to foresee vulnerabilities, ethical hackers are essential in the following areas:
- Safeguards against dangers posed by the internet are being strengthened.
- Protect against identity theft and fraudulent activity.
- Preserving vital information, including individual, financial, and medical details, among other things.
- Aiding organizations in adhering to the different security rules and processes.
The importance of ethical hacking lies in the fact that it safeguards not just businesses but also regular individuals who depend on digital networks for their day-to-day lives, their jobs, and communication.
How Is Ethical Hacking Different from Malicious Hacking?
It is possible that, at first glance, ethical hacking and malicious hacking seem to be comparable due to the fact that both entail testing and breaking into systems. On the other hand, the primary distinction rests in the fact that one is carried out with the intention of safeguarding, while the other is carried out with the intention of causing damage.
Key Differences:
| Aspect | Ethical Hacking (White-Hat) | Malicious Hacking (Black-Hat) |
| Permission | Done with legal approval and authorization | Done without permission, illegal |
| Purpose | To find and fix security flaws | To exploit flaws for personal gain |
| Impact | Protects data, systems, and users | Causes theft, damage, or disruption |
| Outcome | Builds trust and strengthens security | Leads to loss, harm, and legal issues |
| Work Setting | Part of cybersecurity teams, legal projects | Criminal or unauthorized activities |
What Skills Do You Need to Become an Ethical Hacker?
Possessing strong interpersonal and technical skills is essential for an ethical hacker. With these skills, you can safely defend systems while thinking like a hacker.
1. Technical Skills
- Getting a grasp on the basics of networking, which includes protocols like TCP/IP, firewalls, domain name systems (DNS), VPNs, and routers.
- Our operating systems need an in-depth familiarity with Unix, Linux, and Windows.
- An assortment of programming and scripting languages may be found, including Python, C/C++, Java, SQL, JavaScript, and Bash.
- Web technologies include knowledge of database architecture, scripting languages, and HTML, among other building blocks of websites and applications.
- Concepts related to cybersecurity include encryption, social engineering, authentication, and malware.
- Experimenting with a wide range of penetration testing tools, including but not limited to Wireshark, Nmap, Metasploit, and Burp Suite.
2. Transparency Skills
- One definition of a problem-solving mentality is the capacity to analyze issues and propose novel approaches to resolving them.
- Being abreast of the most recent dangers and resources requires an insatiable appetite for knowledge and a dedication to continuing education throughout one’s life.
- To think critically, one must be able to put oneself in the shoes of a system’s attacker and defender.
- One example of communication skills is the ability to clearly explain findings and solutions to others who aren’t technically savvy.
- Being honest and upstanding means taking responsibility for one’s actions and never breaking the law.
3. Credentials (which are commendable but not necessary)
- Membership in the Certified Ethical Hacker (CEH) fraternity
- Certified by CompTIA Security+
- The initials OSCP stand for “Offensive Security Certified Professional.”
- Information Systems Security Professional (CISSP)
How Can Beginners Start Learning Ethical Hacking?
The process of beginning to engage in ethical hacking may seem to be difficult, but with the appropriate technique, novices may gradually increase their abilities. Following is a route map:
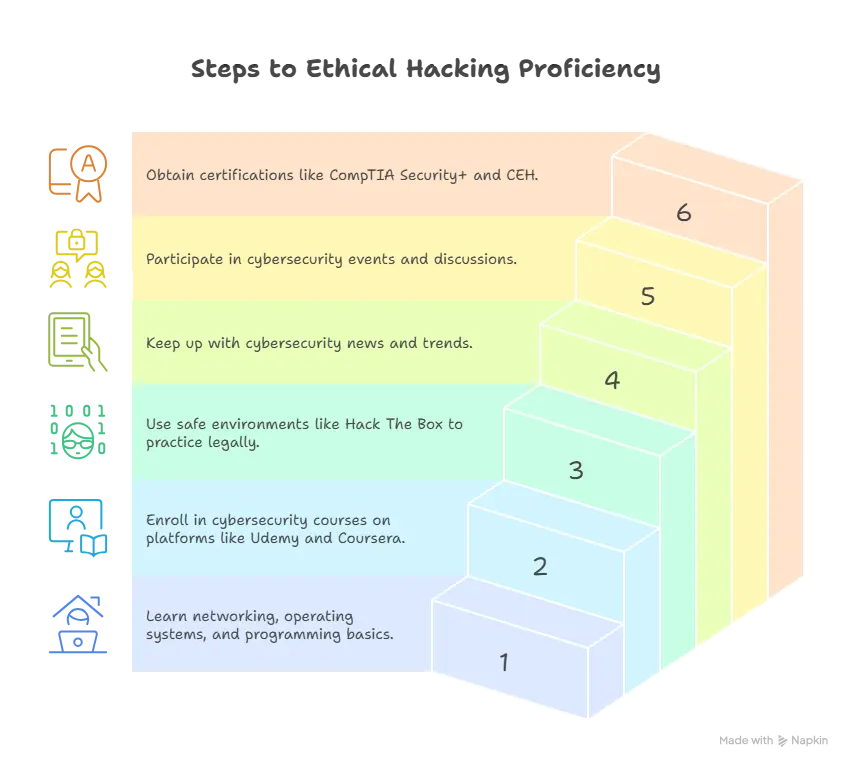
1. Get Familiar with the Fundamentals
Networking and Protocols: Recognize TCP/IP, DNS, HTTP/HTTPS, and Virtual Private Networks (VPNs). Learn how to work in both Windows and Linux settings to get familiarity with operating systems. Learning Python, JavaScript, SQL, or Bash is ideal for automating and testing tasks. Programming and scripting are also important.
2. Enroll in online classes and tutorials
Udemy, Coursera, Cybrary, and LinkedIn Learning are some of the online platforms that provide ethical hacking courses that are suitable for beginners. Examine the availability of classes that address principles of cybersecurity, as well as penetration testing and malware analysis.
3. Follow the law
- Employ safe practice settings such as:
- Hack The Box: Online penetration testing labs.
- TryHackMe: Beginner-friendly tasks with guidance.
- OverTheWire: Wargames to hone security expertise.
4. Read and Remain Current
- Keep up with cybersecurity YouTube channels, blogs, and forums.
- Read the most recent news regarding security, malware, and vulnerabilities.
5. Take part in communities
- Take part in cybersecurity-focused events, online discussions, or Discord groups in your area.
- By taking part in Capture the Flag (CTF) games, you can test your skills and improve.
6. Get the Credits You Need
- For beginners, the following certificates are good:
- Getting certified by CompTIA Security+
- It stands for “Certified Ethical Hacker,” or CEH.
- While OSCP stands for “Offensive Security Certified Professional,”
What Tools and Techniques Are Used in Ethical Hacking?
Ethical hackers use a variety of tools and techniques to test and protect computer systems. These tools help them find security weaknesses, while the techniques show how vulnerabilities can be exploited—safely and legally.
Tools Used by Ethical Hackers
- Nmap: It is a tool that lets you see what devices and services are connected to a network.
- Wireshark: Hackers can use Wireshark to see what data is being sent over a network.
- Metasploit: It is a safe way to check if a system has security holes.
- Burp Suite: It checks websites and web apps for security holes.
- Tools for Cracking Passwords: John the Ripper and other tools like it check for weak passwords.
- Kali Linux: It is a unique operating system that comes with all the tools you need to hack.
Techniques Ethical Hackers Use
- Penetration testing: It means pretending to be a hacker to find holes in security.
- Vulnerability scanning: It means using software to instantly find known security holes.
- Social engineering: It means checking to see if you can get people to give you private information (safely!).
- Testing wirelessly: It means seeing if Wi-Fi networks are safe.
- Web application testing: It means checking websites for bugs like SQL attacks or forms that aren’t safe.
What Career Opportunities Await Ethical Hackers?
As businesses try to defend themselves from cyber dangers, the need for ethical hackers is expanding quickly. There are several employment possibilities for skilled ethical hackers to select from:
1. Penetration Tester
Check systems and networks for weaknesses before bad hackers may take advantage of them.
2. Security Analyst
Checks networks for dangers, finds them, and helps make security stronger overall.
3. A consultant on cybersecurity
Gives companies advice on how to follow the rules, manage risks, and keep their data safe.
4. Incident Responder
Looks into and reacts to cyberattacks to limit harm.
5. Red Team Expert
Tests how effectively security protections operate by pretending to attack systems.
6. Chief Security Officer of Information (CISO)
Oversees the organization’s cybersecurity strategy and security teams.
7. Freelance hacker or bug bounty hunter
Finds security holes on their own and gets paid for them by corporations in a legitimate way.
You might also like: What is Bug Bounty in Cybersecurity?
Enhance your data science skills with us! Join our free demo today!
Conclusion
In today’s digital environment, where cyber risks are always growing, ethical hacking is an extremely important discipline to have. Ethical hackers contribute to the protection of sensitive data, the prevention of financial losses, and the achievement of compliance with security standards by locating and resolving flaws before hostile hackers are able to exploit them. Integrity, curiosity, and a mentality that is focused on finding solutions to problems are also necessary components of ethical hacking, in addition to the technical abilities. At the same time as it contributes to a digital world that is safer and more secure for everyone, it provides novices with an exciting chance to establish a career in cybersecurity that is both important and fulfilling.
Frequently Asked Questions
Do I need a degree to become an ethical hacker?
Not necessarily. While a degree in computer science or IT helps, hands-on skills, practice, and certifications are more important.
Can ethical hackers work independently?
Yes, many ethical hackers work as freelancers or participate in bug bounty programs to find vulnerabilities for rewards.
How long does it take to learn ethical hacking?
It depends on your background. Beginners can learn the basics in 6–12 months with consistent study and practice.
Why is ethical hacking important?
It helps prevent cyberattacks, protects sensitive data, strengthens security systems, and builds trust for organizations and users.
What is a white-hat hacker?
A white-hat hacker is another term for an ethical hacker who uses hacking skills legally to protect systems and data.
Is ethical hacking only for IT professionals?
Not necessarily. Anyone with curiosity, problem-solving skills, and dedication can start learning ethical hacking.