Table of Contents
Social Engineering in Cybersecurity is about hacking people. It focuses on human weakness instead of system weakness. This blog explains how attackers trick human minds. You will learn why social engineering is powerful. We will also cover the common attack techniques. Ethical hackers also use it for security training. By reading, you will understand both risks and defenses. This guide makes cybersecurity knowledge simple and practical.
Social engineering often feels invisible but very dangerous. Hackers use emotions like fear, trust, and curiosity. We will explore how these tactics work in detail. You will also see real-world attack methods explained. The blog shows how to learn ethical techniques. It also explains protection strategies for individuals and companies. Stay alert and aware, because awareness is the shield.
Quick Highlights
- Social engineering is about tricking humans, not systems.
- Hackers use fear, trust, and curiosity to cheat.
- Phishing, baiting, and pretexting are common tricks.
- Ethical hackers learn it to improve protection.
- Training people makes attacks less successful over time.
- Using multi-factor authentication adds strong extra safety.
- Testing staff shows weak points in security habits.
Enroll in Entri’s AI-Powered Cybersecurity course now!
Introduction
Cybersecurity protects systems, data, and personal information. Yet, the biggest weakness is often human behavior. Hackers know people can be tricked very easily. Social engineering uses psychology instead of technical hacking. It manipulates trust, fear, or curiosity for access. These attacks feel normal but hide dangerous intentions. This blog explains social engineering in clear detail. You will also learn defenses against these tricks.
Highlights of This Blog
- Meaning of social engineering in cybersecurity explained.
- Why it is such a strong attack method.
- Common techniques like phishing, baiting, and pretexting.
- How ethical hackers study social engineering safely.
- Ways to protect against human-based cyberattacks.
What Is Social Engineering in Cybersecurity?
Social engineering in cybersecurity targets human psychology. It tricks people instead of attacking machines. Attackers use emotions like fear, trust, and urgency. The goal is to make victims act quickly. This manipulation makes social engineering very dangerous. It can bypass even the strongest digital security. Understanding social engineering helps people build strong defenses.
How Social Engineering Differs from Hacking
Traditional hacking targets systems, software, or networks. It exploits coding errors or technical weaknesses directly. Social engineering, however, manipulates human decision-making instead. It relies on convincing someone to give access. Both hacking types are dangerous but work differently.
Comparison Table: Hacking vs Social Engineering
| Aspect | Hacking | Social Engineering |
|---|---|---|
| Target | Software, systems, or networks | Human psychology and behavior |
| Method | Exploits code or system vulnerabilities | Exploits trust, fear, or urgency |
| Tools Used | Malware, exploits, scripts, programs | Emails, phone calls, fake identities |
| Main Weakness Attacked | Technology flaws | Human judgment and emotions |
| Defense | Firewalls, patches, antivirus | Awareness, training, verification |
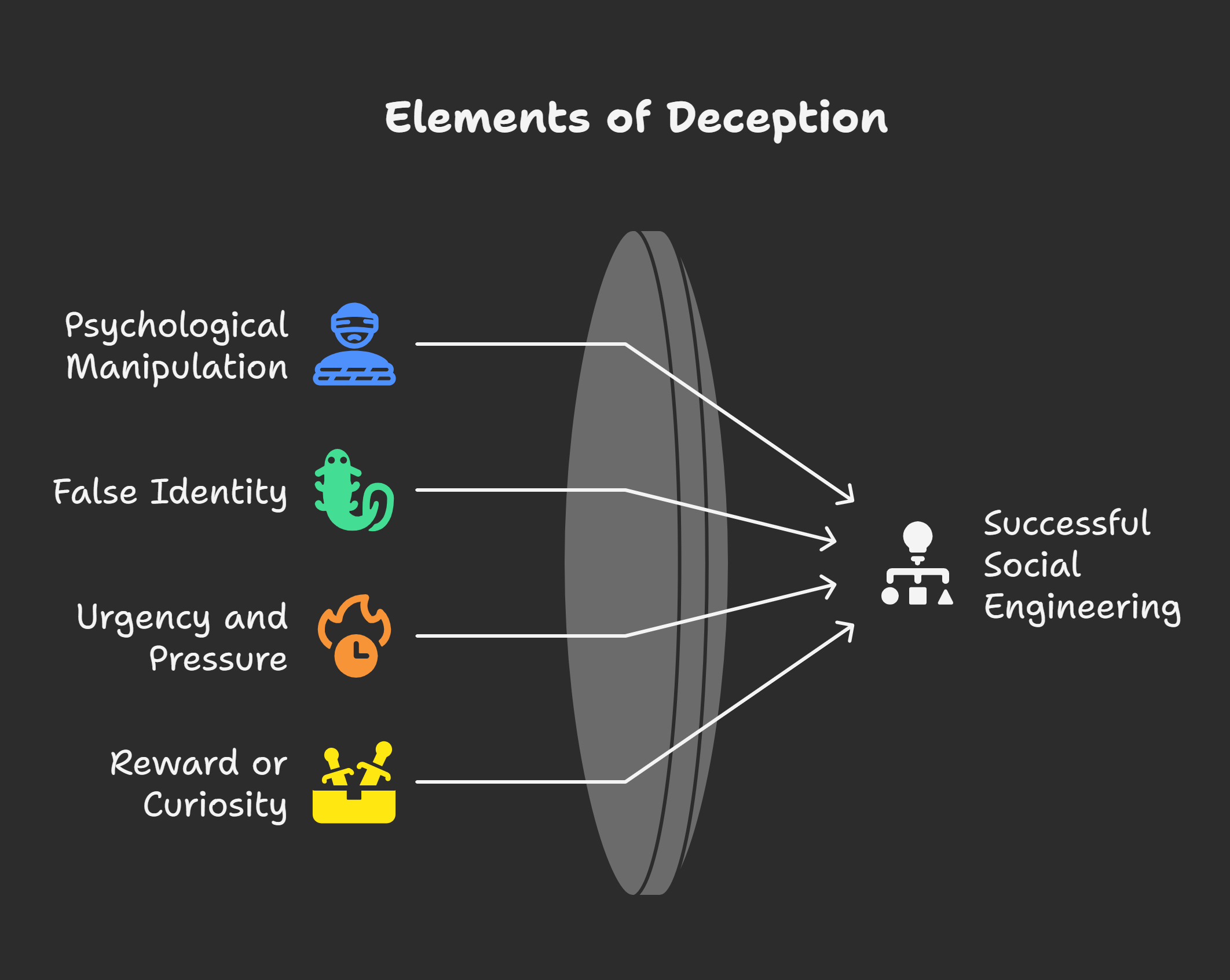
Core Elements of Social Engineering
- Psychological Manipulation
- Attackers study how people usually react.
- They use trust, fear, or curiosity effectively.
- False Identity or Pretext
- Attackers pose as authority or known staff.
- This gains credibility and lowers suspicion levels.
- Urgency and Pressure
- Messages often say “act immediately or lose.”
- Fear makes people skip careful verification steps.
- Reward or Curiosity
- Baits like free downloads attract quick action.
- Curiosity often pushes users to take risks.
Why Social Engineering Works So Effectively
Humans trust familiar sources more than unknown ones. Hackers exploit this by pretending to be trusted. Emotions often override logic in stressful situations. People also value speed over careful verification sometimes. Attackers know and exploit these natural human patterns. This makes attacks harder to detect or stop. Technology cannot fully guard against human error.
Real-Life Example of Social Engineering
A hacker may send a fake bank email. The email warns about account suspension or closure. It requests immediate login for “security verification.” A worried user enters details without second thought. The attacker now has full account access. Here, no system hack was needed at all. The mind was hacked instead of technology.
Importance of Understanding Social Engineering
- For Individuals
- Helps protect personal data from attackers.
- Builds awareness against suspicious messages daily.
- Encourages safer habits online and offline.
- For Organizations
- Reduces risks of insider leaks and fraud.
- Strengthens overall cybersecurity beyond technology.
- Supports training programs for staff awareness.
- For Ethical Hackers
- Provides insights into human vulnerabilities clearly.
- Enables testing and training for stronger defenses.
- Helps organizations understand real-world risks better.
Final Thoughts on Social Engineering
Social engineering is hacking through human interaction. It relies on manipulation, not advanced coding skills. Attackers find it cheaper and faster than hacking. That makes it a growing global cybersecurity concern. Awareness and education remain the strongest possible defenses. People must think before trusting unknown requests. Every informed decision reduces risks of manipulation.
Enroll in Entri’s AI-Powered Cybersecurity course now!
Why Is Social Engineering a Powerful Cybersecurity Technique?
Social engineering is powerful because it targets humans. It exploits emotions instead of breaking digital defenses. Hackers know people are often careless under pressure. This makes attacks faster and cheaper than hacking. Technology cannot always prevent human-based manipulation attempts. That is why social engineering succeeds so often. It remains a top threat in cybersecurity today.
Human Psychology as the Weak Point
People naturally trust familiar names and organizations. Hackers exploit this trust for personal gain. Fear and urgency often push people to act. Curiosity can also make people ignore warnings. These instincts are hard to override quickly. Attackers manipulate these instincts for maximum success.
Technology Cannot Fully Stop Social Engineering
Firewalls block unauthorized traffic but not fake emails. Antivirus detects malware but not manipulated conversations. Encryption protects data but not shared credentials. Humans remain the weakest link in every defense. Social engineering bypasses tools by targeting human error. This makes technology alone insufficient against such attacks.
Table: Why Technology Fails Against Social Engineering
| Security Measure | Works Against Technology | Fails Against Humans |
|---|---|---|
| Firewalls | Blocks malicious traffic | Cannot block fake requests |
| Antivirus Software | Detects harmful programs | Cannot stop emotional pressure |
| Encryption | Secures stored data | Cannot stop password sharing |
| Multi-factor Auth | Adds login protection | Still bypassed if user fooled |
Advantages for Attackers Using Social Engineering
- Low Cost
- Requires minimal tools compared to software exploits.
- An email or phone call is often enough.
- High Success Rate
- People often fail to detect manipulation.
- Urgency or fear creates instant responses.
- Less Risk of Detection
- Attacks look like normal interactions usually.
- No suspicious code is required to execute.
- Direct Access to Information
- Victims provide data willingly without resistance.
- Attackers skip many traditional security barriers.
Real-World Reasons Behind Its Effectiveness
- Speed: A single message can compromise multiple users.
- Scalability: Phishing can reach thousands instantly.
- Flexibility: Attackers adapt messages to different victims.
- Global Reach: Internet makes victims easily accessible worldwide.
- Human Error: One careless act can break systems.
These reasons show why attackers prefer social engineering strongly.
Example: Fake IT Support Call
An attacker pretends to be company IT support. They claim a system issue requires urgent fixing. The employee shares login details without further checks. The attacker now controls sensitive business systems. No technical hacking was involved in this attack. The entire breach relied on employee trust only.
Why Organizations Should Care Deeply
- Financial Losses
- Social engineering often causes fraud or theft.
- Recovery usually costs huge amounts of money.
- Reputation Damage
- Customers lose trust after data breaches.
- Brand image takes long to rebuild afterward.
- Operational Disruptions
- Attackers can disable services through manipulation.
- Staff productivity suffers due to fake incidents.
- Legal and Compliance Risks
- Data leaks may violate privacy laws globally.
- Companies face penalties for weak protections.
Final Thoughts on Its Power
Social engineering thrives because humans are predictable. Attackers need no coding skills to succeed. They only need confidence and strong communication tactics. This makes it more dangerous than technical hacking. Strong awareness training reduces these attack success rates. Educated users are the hardest targets for manipulation. People, not firewalls, are the ultimate line.
What Are the Most Common Social Engineering Techniques?
Social engineering uses many tricks to fool people. Attackers carefully design methods to exploit human behavior. Some techniques rely on technology, others use conversation. Every method has the same final goal: access. These attacks remain common because they often succeed. Learning them helps people identify danger more easily. Let us explore the most popular techniques.
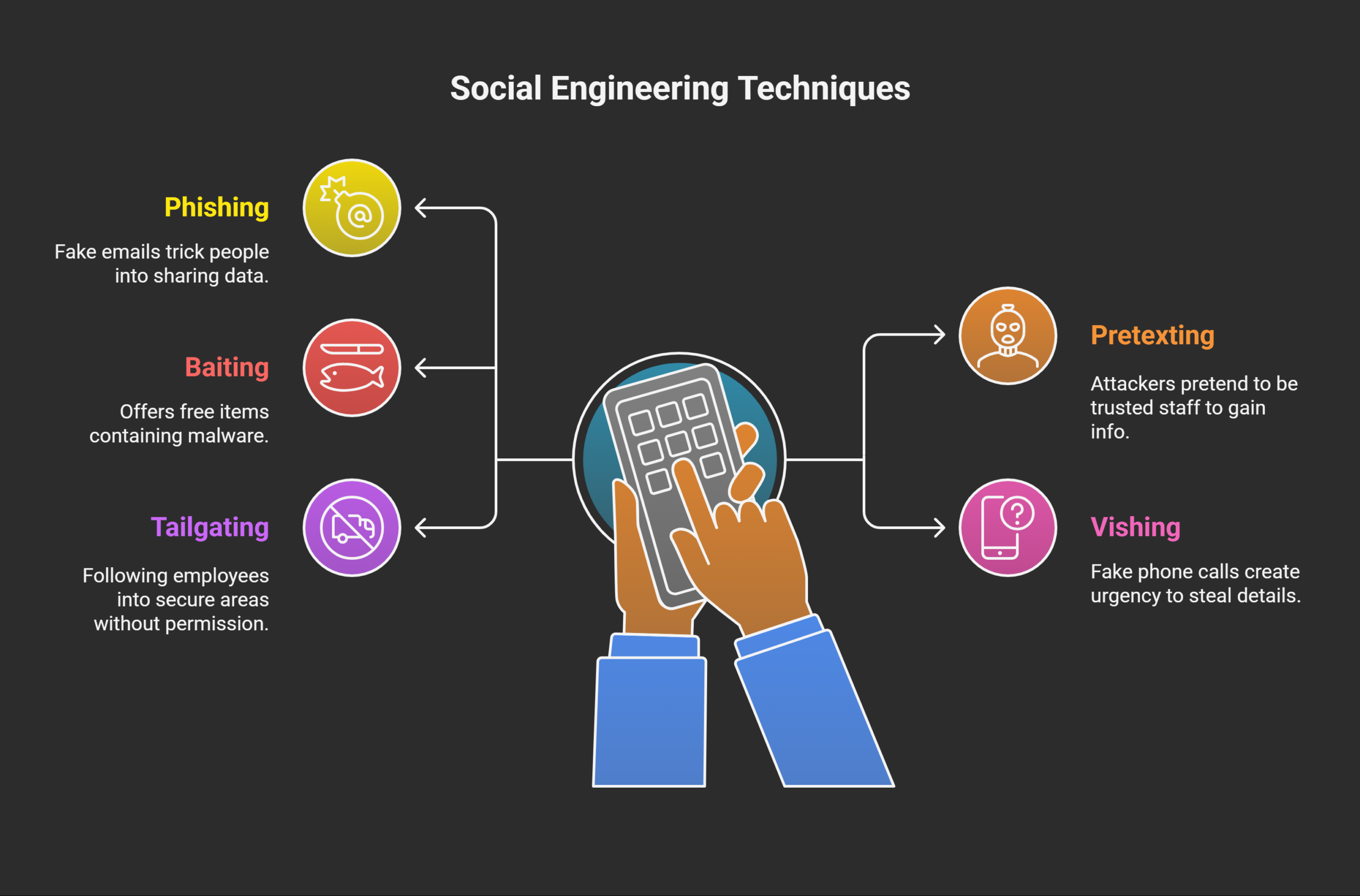
Phishing
Phishing is the most common social engineering method. Attackers send fake emails or text messages daily. These messages often look real and convincing. Victims click links or share sensitive personal data. Phishing can target thousands of people very quickly.
Example: A fake email claims “bank account locked.”
The user enters details on a fake website.
Attackers then collect passwords and access real accounts.
Pretexting
Pretexting involves building a false story first. Attackers pretend to be authority or trusted staff. They use this false role to gain information. Victims often share data without proper verification steps.
Example: Someone pretends to be HR requesting details.
The employee trusts them and shares private records.
The attacker now has sensitive company data.
Baiting
Baiting uses curiosity or greed to trap victims. Attackers offer free items that actually contain malware. This works both online and in physical spaces.
Example: A USB labeled “confidential salary list” is left.
An employee plugs it into a work computer.
The system gets infected with hidden malware.
Vishing (Voice Phishing)
Vishing attacks use phone calls to trick victims. Attackers pretend to be bank staff or officials. They create urgency to collect account details quickly. Victims trust the voice and share private information.
Example: Caller says “your account is compromised today.”
The victim provides card details to fix issue.
The attacker then empties the account easily.
Tailgating
Tailgating is a physical social engineering method. Here, attackers follow employees into restricted areas. They act innocent, like forgetting their access card. Victims often hold doors open without questioning identity.
Example: A hacker follows staff into a server room.
No one asks for ID or access proof.
The attacker now has direct system access.
Table: Techniques, Goals, and Real-Life Examples
| Technique | Main Goal | Real-Life Example |
|---|---|---|
| Phishing | Steal credentials quickly | Fake bank email with login link |
| Pretexting | Gain trust and information | Fake HR staff requesting employee data |
| Baiting | Deliver malware silently | USB labeled “confidential salary list” |
| Vishing | Collect details by voice | Fake bank call about compromised account |
| Tailgating | Enter restricted areas | Attacker follows staff into server room |
Why These Techniques Succeed Often
- Realistic Messages: Emails or calls look very genuine.
- Emotional Pressure: Fear and urgency make victims panic.
- Natural Habits: People often trust authority without question.
- Curiosity Factor: Free items or secrets attract attention.
- Politeness Norms: Staff rarely deny entry to strangers.
These human behaviors make techniques highly successful globally.
Final Thoughts on Common Techniques
These techniques remain the backbone of social engineering. Attackers use them because they are simple and cheap. No advanced coding knowledge is required to apply them. Awareness training reduces the risk of falling victim. Recognizing patterns makes attacks easier to avoid. Everyone must stay cautious about unexpected requests daily. A careful mind is the strongest defense.
How Can You Learn Social Engineering as an Ethical Hacker?
Ethical hackers study social engineering to strengthen defenses. They learn attacker tricks to protect real systems. This knowledge helps organizations avoid major security breaches. Learning social engineering also builds awareness of psychology. It shows how hackers manipulate human emotions daily. Practical training makes learning effective and realistic. Let us explore different ways to learn.
Formal Cybersecurity Courses
Many institutes teach social engineering in ethical hacking. Courses include real-world attack case studies and examples. They provide guided practice in a safe environment. Learners gain certifications proving strong professional knowledge.
Examples of Popular Training Courses
- CEH (Certified Ethical Hacker)
- OSCP (Offensive Security Certified Professional)
- CompTIA Security+ with social engineering modules
These courses combine theory, labs, and simulation projects.
Simulation and Phishing Exercises
Simulated phishing emails train ethical hackers practically. They design fake emails to test employee awareness. This shows how easily staff can be fooled. It also highlights weak areas needing more training.
Example: Create fake company “password reset” emails.
Send them to staff as awareness exercises.
Record how many actually click on links.
These simulations help measure human risk accurately.
Social Engineering Toolkits
Special software helps simulate real social engineering attacks. These toolkits allow ethical hackers to test defenses. They include templates for phishing, vishing, and baiting. Using them shows organizations real risks in practice.
Examples of Popular Tools
- SET (Social Engineering Toolkit): Widely used penetration testing tool.
- GoPhish: Open-source platform for phishing campaigns.
- Evilginx2: Advanced phishing tool for credential capture.
These tools are for legal, controlled environments only.
Learning Human Psychology
Social engineering is less about code, more psychology. Understanding behavior improves manipulation and defense detection skills. Ethical hackers study how trust is built quickly. They also analyze decision-making under pressure and fear.
Practical Approaches
- Reading books on persuasion and human behavior.
- Observing communication patterns in real workplaces.
- Studying famous psychological experiments about authority influence.
This knowledge makes training more realistic and practical.
Workshops and Security Drills
Organizations conduct workshops on social engineering attacks. These include role-playing real scenarios with employees. Hackers act as attackers, staff act as targets. Everyone learns by experiencing attacks in controlled settings.
Example: Simulate a stranger tailgating into office buildings.
Check how many employees allow entry without checking.
Later, discuss why such behavior is risky.
Workshops create awareness through live practical experiences.
Table: Practical Training Methods for Ethical Hackers
| Training Method | Example Tool / Practice | Learning Outcome |
|---|---|---|
| Cybersecurity Courses | CEH, OSCP, CompTIA Security+ | Certified knowledge of social engineering |
| Phishing Simulations | Fake company email campaigns | Measure and improve staff awareness |
| Social Engineering Toolkits | SET, GoPhish, Evilginx2 | Test systems using realistic attack setups |
| Psychology Study | Persuasion books, behavior analysis | Understand human vulnerabilities |
| Workshops and Drills | Tailgating or vishing role-play | Real-life learning through active practice |
Why Practical Learning Matters
Practical training makes ethical hackers think like attackers. It prepares them to anticipate tricks before happening. Real-world simulations show how humans behave under stress. This builds stronger defense strategies inside organizations. Theory alone cannot prepare hackers for real threats. Hands-on practice remains the most valuable learning approach.
Final Thoughts on Learning Social Engineering
Ethical hackers must study social engineering carefully. It gives them skills to protect organizations effectively. Practical training methods ensure lessons are memorable. Tools, simulations, and workshops make learning realistic. Understanding psychology completes the knowledge of hacking methods. This balanced approach strengthens both people and technology. A trained mind can outsmart manipulative attackers.
How Can You Protect Against Social Engineering Attacks?
Social engineering attacks cannot be stopped by tools alone. They need a balance of human and technical defenses. Attackers target people, but also exploit weak systems. Organizations must build layers of protection for safety. Individuals must also stay alert in daily activities. Both awareness and technology play equal important roles. Let us explore practical ways to protect.
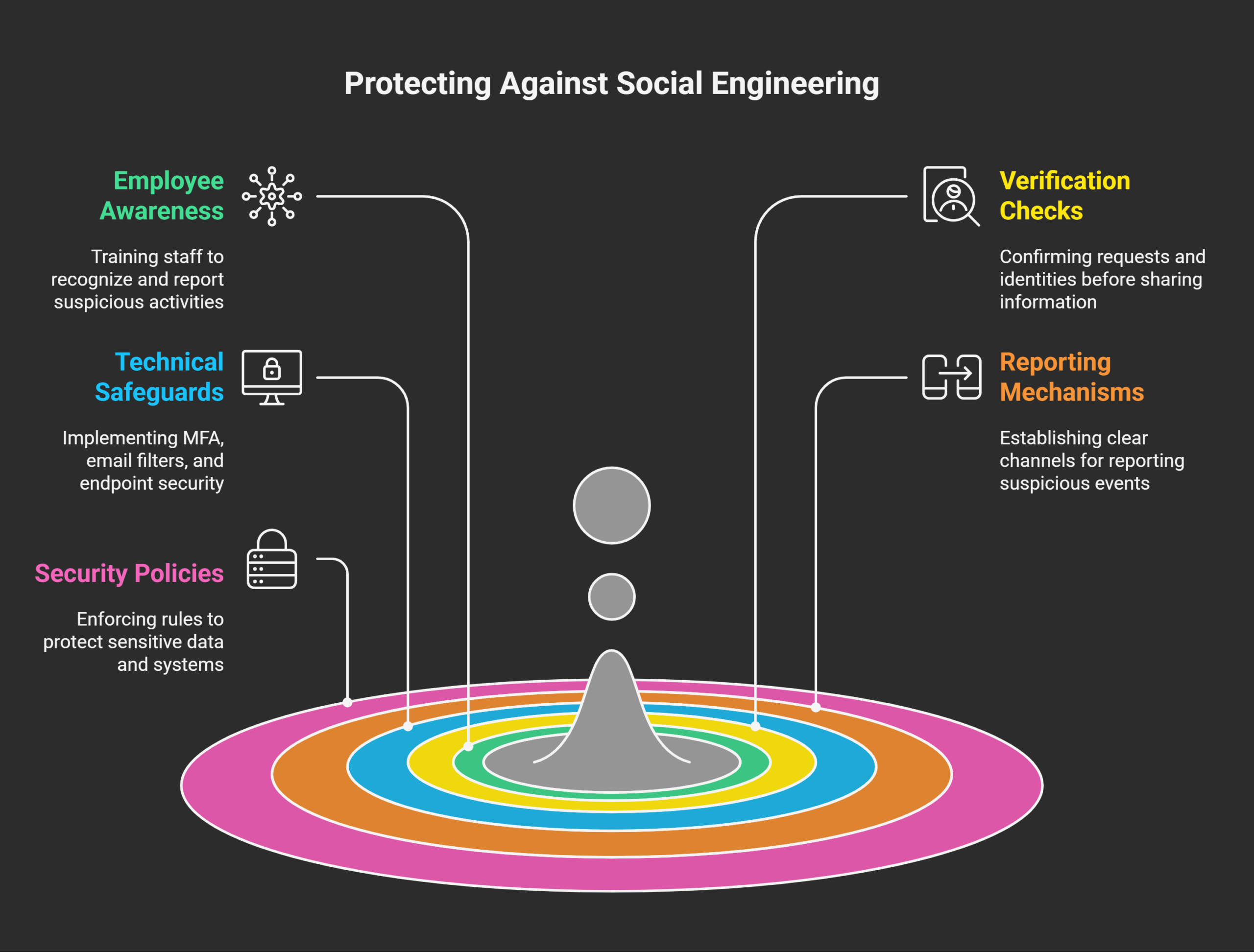
Employee Awareness and Training
Employees are the first line of defense. Training helps them identify suspicious behavior or messages. Regular awareness programs reduce the risk of mistakes. Phishing tests also improve recognition of fake emails.
Example: Conduct monthly phishing email simulations. Discuss results openly and share safety tips.
This builds stronger habits across the organization.
Verification and Identity Checks
Always verify requests before sharing any sensitive information. Employees must confirm details through secondary trusted channels. Verification should apply to emails, calls, or visitors.
Practical Approaches
- Call back using official company numbers.
- Double-check unusual requests with supervisors.
- Request written confirmation for sensitive data access.
These steps stop attackers pretending as authority figures.
Technical Safeguards
Technology adds another protective layer against attacks. It helps reduce damage even if people fail. Strong systems make manipulation less likely to succeed.
Important Safeguards
- Multi-factor Authentication (MFA): Protects accounts beyond stolen passwords.
- Email Filters: Detect suspicious or spam-like communication.
- Endpoint Security: Blocks malware from baiting devices.
- Access Controls: Limit who can view sensitive data.
These measures make attacks harder and slower.
Reporting and Response Mechanisms
Quick reporting reduces damage after an attack. Employees must know how to report suspicious events. Organizations should build clear response procedures for staff.
Example: Dedicated hotline for phishing attempts reporting. Security teams can investigate cases immediately afterward.
This helps contain risks before they spread further.
Security Policies and Rules
Policies create structure for employee security behavior. They define what is acceptable or dangerous behavior. Clear rules reduce confusion during stressful situations.
Examples of Policies
- Do not share passwords over phone or email.
- Always lock systems before leaving your desk.
- Report strangers without badges in secure areas.
Policies remind people of expected safe practices daily.
Balanced Protection Table
| Protection Method | Focus Area | Example Application |
|---|---|---|
| Awareness Training | Employee Behavior | Monthly phishing simulations for staff |
| Verification Practices | Employee Decisions | Confirming requests through trusted numbers |
| Multi-factor Authentication | Technical Security | Login protection beyond stolen passwords |
| Email Filtering | Technical Security | Blocking fake emails from inboxes |
| Security Policies | Employee Habits | Rules on password and access sharing |
| Incident Reporting | Organizational Response | Hotline for reporting phishing attempts |
Why Balance Is Important
Only technical tools cannot stop human mistakes. Only awareness cannot stop advanced digital intrusions. A combination ensures stronger, complete security coverage. Balance reduces risks from multiple possible attack angles. Both employees and systems share equal responsibility.
Final Thoughts on Protection
Social engineering attacks will always try to continue. But people and systems can block most attempts. Awareness programs build alert and confident employees. Technology tools add reliable backup against human error. Policies and reporting ensure structure in tough moments. Balanced protection makes organizations harder to manipulate. Together, humans and systems build the strongest defense.
Conclusion
Social engineering in cybersecurity targets the human mind. It shows that people can be tricked easily. Attackers use fear, curiosity, or trust for access. No system is safe if people are careless. Awareness and training create the strongest human firewall. Technology adds another barrier against these manipulations. Together, they reduce risks and protect sensitive data.
Everyone must play a role in security defense. Employees must stay alert in daily digital activities. Organizations must invest in both tools and training. Simple rules, strong systems, and quick reporting help. Balanced protection ensures fewer successful cyberattacks over time. Stay alert, because prevention always beats recovery later. Stronger awareness today means safer systems tomorrow.
| Related Articles | |
| Entri Launched AI-Powered Cybersecurity Course | Cybersecurity Career Path |
| An Introduction to Cybersecurity Ethics | Top Cybersecurity Languages to Learn |
Frequently Asked Questions
What does social engineering in cybersecurity mean?
Social engineering in cybersecurity refers to the manipulation of individuals rather than systems to gain unauthorized access to information, systems, or resources. Instead of breaking through firewalls or software, attackers exploit human psychology, such as trust, fear, or curiosity. These tactics make social engineering one of the most dangerous forms of cyberattacks.
What are the most common examples of social engineering attacks?
The most common types of social engineering include phishing emails, pretexting, baiting, and tailgating. Phishing remains the most widespread, where fake messages trick people into sharing sensitive details. Baiting uses physical or digital temptations, such as infected USB drives, while tailgating exploits trust to gain unauthorized entry to physical spaces.
Why is social engineering considered more dangerous than technical hacking?
Social engineering is often considered more dangerous because even the most advanced security systems cannot fully prevent human mistakes. A single careless click on a phishing email or a rushed decision in response to a fake phone call can compromise entire networks. Unlike technical hacking, social engineering requires little technical knowledge but can cause enormous damage.
How do attackers succeed in social engineering?
Attackers succeed by exploiting natural human behaviors and emotions. They often create scenarios that involve urgency, fear, or authority, which pressure victims into quick decisions. For example, an attacker might impersonate a bank representative, asking for login credentials under the guise of solving an urgent issue.
Can social engineering attacks be prevented completely?
No, social engineering cannot be completely prevented, but risks can be minimized. Continuous employee training, strong policies, and technical safeguards make attacks much harder to succeed. A layered defense strategy ensures that even if one measure fails, others remain in place to protect systems.
What role does employee training play in prevention?
Employee training plays a central role in preventing social engineering attacks. Well-informed employees can recognize suspicious requests, report incidents quickly, and resist manipulation. Regular workshops, phishing simulations, and awareness campaigns keep staff updated on evolving tactics used by attackers.
What steps should individuals take to stay safe?
Individuals should verify all unusual requests, avoid clicking unknown links, and never share sensitive information over phone or email without proper checks. They should also enable multi-factor authentication and stay alert to unexpected communication, especially those creating urgency or fear. Personal vigilance is as important as organizational defense.
How can organizations use technology to defend against these attacks?
Organizations can implement multiple layers of technology to reduce risks. Tools such as multi-factor authentication, spam filters, endpoint protection, and access controls limit opportunities for attackers. While technology alone cannot stop social engineering, it creates strong barriers that make manipulation less effective.
Why should organizations treat social engineering as a priority?
Organizations should treat social engineering as a priority because it targets the most unpredictable element—people. Technical defenses are important, but one employee mistake can bypass them all. Prioritizing training, awareness, and a balance of human and technological defenses ensures stronger, more reliable cybersecurity.
How do ethical hackers learn about social engineering?
Ethical hackers study social engineering to strengthen defense strategies. They use controlled simulations and penetration tests to identify weaknesses in organizations. By practicing these techniques ethically, they can recommend stronger training, awareness programs, and technical safeguards to reduce risks.