Table of Contents
Have you ever wondered why Linux is essential for ethical hacking? Do you know why most hackers avoid Windows for hacking tasks? Have you heard of Kali Linux or Parrot OS before? Many beginners get confused about where to start with Linux. Do you feel Linux commands look too hard at first sight? What if learning Linux could actually be easier than you think? This blog will clear those doubts step by step for you. You will see why Linux matters in hacking and how to begin. By the end, you will know the right tools and paths to follow.
This blog will answer your common questions in detail. You will explore what makes Linux different from other systems. We will discover the best Linux distributions for hacking. You will also see the tools that run on Linux. Step-by-step tips for beginners will be included. We will also show how a course can guide you. Career benefits of learning Linux for hacking will be explained. Finally, you will leave with a clear roadmap to get started.
Key Takeaways
- Learn why Linux is essential for ethical hacking.
- Understand how Linux differs from other systems.
- Explore the best Linux distributions for hackers.
- Discover key ethical hacking tools on Linux.
- Get beginner tips to start learning Linux.
- See how a course can guide your journey.
- Know the career benefits of mastering Linux.
Enroll in Entri’s AI-Powered Cybersecurity course now!
Introduction
Ethical hacking is growing fast in today’s digital world. Hackers need strong systems to test networks and software. Linux provides stability, flexibility, and unmatched security features. It supports most penetration testing and security analysis tools. Ethical hackers trust Linux for reliable and safe operations. Its open-source design makes it transparent and customizable. That is why it is the preferred hacking platform.
Key Points:
- Ethical hacking demand is rising in all industries.
- Professionals must secure systems from increasing cyber threats.
- Linux is widely adopted in cybersecurity worldwide.
- Training programs prioritize Linux for hacking practice.
- Learning Linux builds a strong foundation for hacking.
Why Is Linux Essential for Ethical Hacking?
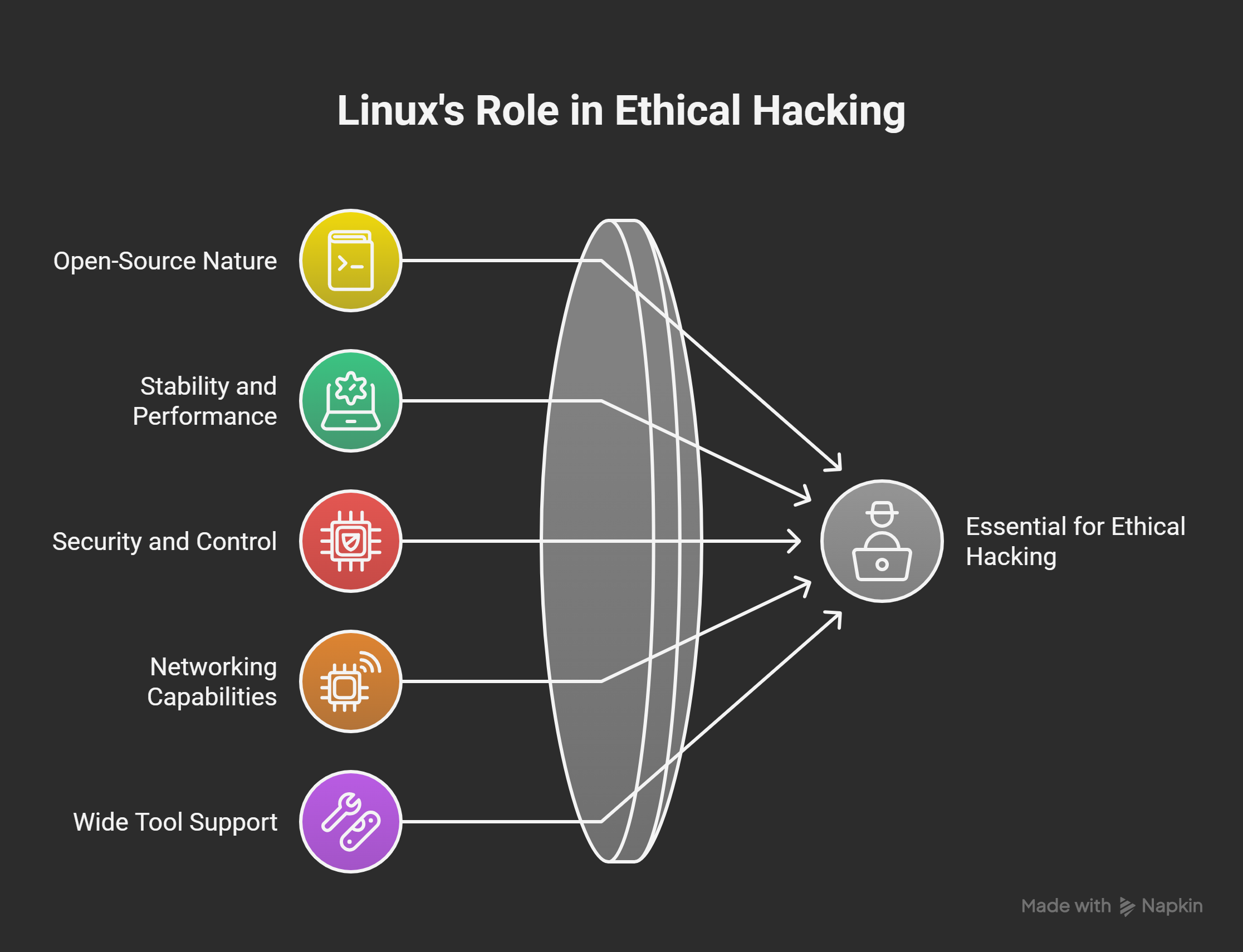
Linux is the most used system in ethical hacking. It is simple, powerful, and trusted by professionals worldwide. Hackers prefer Linux because it gives more control. It is free, open-source, and easy to customize. Linux is also very stable and rarely crashes. This makes it safe for running heavy hacking tools. That is why Linux is essential for ethical hacking.
1. Open-Source Nature
Linux is fully open-source and accessible for everyone. Anyone can study, edit, and modify the source code. This freedom allows hackers to create unique security solutions. It also helps understand how systems actually function. Windows and macOS hide many system-level processes. Linux reveals everything, which builds strong technical knowledge.
2. Stability and Performance
Linux is stable and rarely crashes during heavy tasks. It works efficiently on both new and old hardware. Ethical hackers often run many tools at once. Linux ensures smooth performance even under heavy workloads. It also consumes fewer resources compared to Windows. This means more power for penetration testing tools.
3. Security and Control
Linux gives complete control over system security settings. Users can manage permissions, processes, and system configurations. This makes it safer for testing risky exploits. Ethical hackers often work with sensitive systems. Linux allows them to isolate risks safely. This control reduces chances of harming real systems.
4. Networking Capabilities
Linux is strong in networking compared to other systems. It comes with built-in commands for monitoring networks. Hackers can analyze traffic, ports, and vulnerabilities easily. Networking tools run faster and more reliably on Linux. This makes it ideal for penetration testing servers. It also simplifies advanced wireless security experiments.
5. Wide Tool Support
Most hacking tools are developed for Linux first. Tools like Nmap, Metasploit, and Wireshark work flawlessly here. Special distributions like Kali come preloaded with these tools. This saves hackers effort in installing everything manually. Windows often requires adjustments for tool compatibility. Linux ensures direct, smooth operation without extra steps.
Table: Key Features of Linux for Ethical Hacking
| Feature | Benefit for Hackers |
|---|---|
| Open-source | Full freedom to customize systems |
| Stability | Rare crashes during heavy testing |
| Performance | Runs smoothly on low hardware |
| Security | Strong control over permissions |
| Networking | Advanced built-in commands |
| Tool support | Works with most hacking tools |
Key Points Recap
- Linux is open-source and transparent.
- It provides stability under heavy loads.
- Offers strong user security control.
- Delivers advanced networking features.
- Supports nearly all major hacking tools.
What Makes Linux Different from Other Operating Systems for Hacking?
Linux stands out as the most hacker-friendly operating system. It offers freedom, flexibility, and transparency other systems restrict. Hackers can explore, modify, and control Linux deeply and safely. This makes it very different from Windows or macOS. Linux is not only a system but a full toolkit. It allows hackers to learn, test, and practice effectively. Let us explore what makes Linux truly different.
1. Open-Source Advantage
Linux is fully open-source and free to use. Windows and macOS are closed and limit user freedom. Open-source allows hackers to customize their environment easily. This transparency makes Linux more suitable for experiments.
2. Lightweight and Resource Friendly
Linux can run smoothly on very old machines. It uses fewer resources compared to heavy systems. Hackers can run multiple tools without performance drops. This efficiency helps during advanced penetration testing tasks.
3. Command-Line Power
Linux provides a powerful command-line interface (CLI). Windows depends mostly on a graphical interface. CLI gives hackers faster and deeper system access. It also supports automation through Bash scripting.
4. Better Networking Support
Linux includes many networking tools by default. It supports advanced scanning, monitoring, and traffic analysis. Hackers can test servers and wireless systems easily. Other systems often need extra software for such tasks.
5. Tool Compatibility
Most hacking tools are designed for Linux first. Popular tools include Nmap, Hydra, Wireshark, and Metasploit. Distributions like Kali come with hundreds pre-installed. Windows often struggles with compatibility issues.
Table: Linux vs Other Systems for Hacking
| Feature | Linux Benefit | Other Systems Limitation |
|---|---|---|
| Open-source | Fully customizable | Closed and restricted |
| Resource usage | Runs on old machines | Needs more hardware power |
| Command-line | Strong CLI and scripting | Weak or limited CLI |
| Networking tools | Built-in and advanced | Requires extra installations |
| Tool support | Broad and reliable | Limited or less stable |
Key Points Recap
- Linux is open-source and transparent.
- It runs fast on old hardware.
- CLI gives hackers deep system control.
- Networking features are advanced and built-in.
- Most hacking tools support Linux best.
Which Linux Distributions Are Best for Ethical Hacking?
Not all Linux systems are the same for hacking. Different distributions are built for different hacking purposes. Some are heavy with preloaded tools, others are lightweight. Choosing the right one depends on your learning stage. Beginners may prefer simple systems with fewer complexities. Advanced users may need large tool collections pre-installed. Let us explore the best Linux distributions for hackers.
1. Kali Linux
Kali Linux is the most popular hacking distribution. It comes with hundreds of security tools pre-installed. Tools cover penetration testing, forensics, and wireless attacks. Kali is regularly updated and widely used by professionals. It also supports ARM devices, cloud, and virtual machines. Beginners like Kali because everything is ready to use. However, it can be heavy for very old hardware.
Key Highlights:
- Over 600 pre-installed security tools.
- Regular updates from Offensive Security.
- Strong community support for beginners.
- Best for learning penetration testing quickly.
2. Parrot Security OS
Parrot Security OS is lightweight and privacy-focused. It uses fewer resources compared to Kali Linux. Parrot comes with security, forensics, and anonymity tools. It is based on Debian, like Kali Linux. Parrot is great for hackers who value speed. It also includes privacy tools like Tor and Anonsurf. This makes it strong for both hacking and anonymity.
Key Highlights:
- Lightweight and faster than Kali.
- Privacy tools built into the system.
- Supports ethical hacking and digital forensics.
- Good for mid-level and privacy-focused users.
3. BlackArch Linux
BlackArch is built for advanced penetration testers. It has over 2,500 hacking tools available. It is based on Arch Linux and customizable. BlackArch is not beginner-friendly due to complexity. It needs strong Linux knowledge to use effectively. Advanced hackers enjoy its flexibility and tool variety.
Key Highlights:
- Very large tool collection.
- Highly customizable and flexible.
- Designed for advanced professionals.
- Requires strong Linux knowledge.
4. BackBox Linux
BackBox is simple, lightweight, and stable. It is based on Ubuntu, making it beginner-friendly. It has essential hacking and security tools included. BackBox focuses on speed and reliability for testing. It is perfect for learning without overwhelming tools.
Key Highlights:
- Easy to use for beginners.
- Runs smoothly on old machines.
- Includes essential penetration tools.
- Best for stable and fast operations.
5. DEFT Linux
DEFT stands for Digital Evidence and Forensic Toolkit. It is designed mainly for forensic investigations. It includes tools for data recovery and analysis. Hackers use DEFT for investigating cybercrimes. It is less popular but strong for investigations.
Key Highlights:
- Focus on digital forensics and recovery.
- Easy to use for evidence analysis.
- Specialized distribution for investigators.
- Good addition to hacker’s toolkit.
Table: Popular Linux Distributions for Ethical Hacking
| Distribution | Best For | Key Strengths |
|---|---|---|
| Kali Linux | Beginners, professionals | Preloaded tools, strong support |
| Parrot OS | Privacy-focused hackers | Lightweight, includes anonymity tools |
| BlackArch Linux | Advanced penetration testers | Huge toolset, customizable |
| BackBox Linux | Beginners, light hardware users | Simple, stable, fast |
| DEFT Linux | Forensic investigators | Evidence analysis, data recovery |
Key Points Recap
- Kali Linux is best for all-round penetration testing.
- Parrot OS is light, private, and fast.
- BlackArch is advanced with thousands of tools.
- BackBox is stable and great for beginners.
- DEFT Linux is best for forensic investigations.
Enroll in Entri’s AI-Powered Cybersecurity course now!
How to Choose the Right Linux Distribution for Yourself?
Choosing a Linux distribution may seem confusing at first. There are many options with different features and purposes. Some are light, some are powerful, and some focus on hacking tools. Beginners should not feel overwhelmed. The best way is to follow a clear process. A step-by-step guide makes it easier. Let’s go through the steps below.
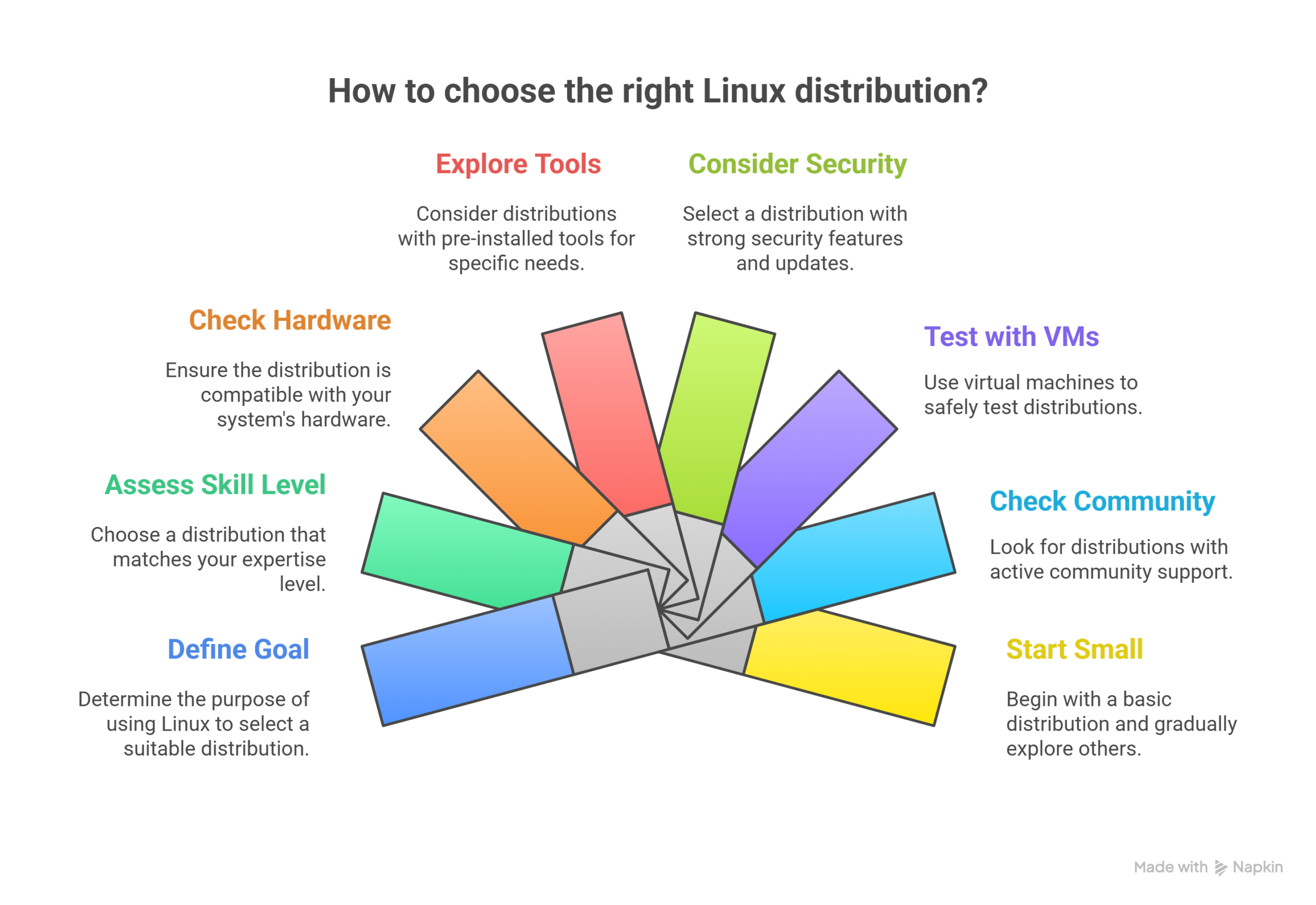
1. Know Your Goal
- Decide why you need Linux.
- Is it only for ethical hacking practice?
- Do you also want daily system use?
- Different goals need different distributions.
2. Check Your Skill Level
- Beginners need user-friendly systems.
- Advanced users can handle complex systems.
- Pick easy options like Kali or Parrot first.
- Move to advanced ones once you gain skill.
3. Look at Hardware Needs
- Some distributions need high system resources.
- Old systems may not run heavy distributions well.
- Light options like Parrot Home use fewer resources.
- Always check system requirements before installing.
4. Explore Pre-installed Tools
- Kali offers many hacking tools pre-installed.
- Parrot also includes privacy and forensic tools.
- BlackArch provides a massive tool collection.
- Beginners may prefer ready-to-use toolkits.
5. Think About Security Features
- Good hacking distributions focus on security.
- Parrot OS offers sandboxing features.
- Kali provides frequent tool updates.
- Choose systems that protect you while testing.
6. Test with Virtual Machines
- Use VirtualBox or VMware for testing.
- Try different distributions safely in VMs.
- This avoids harming your main system.
- Testing helps you choose more confidently.
7. Consider Community Support
- Strong communities help with issues.
- Kali has huge community and tutorials.
- Parrot has active forums and guides.
- Check support before final choice.
8. Start Small, Then Expand
- Begin with one beginner-friendly distribution.
- Explore tools and basic commands first.
- Later, try advanced distributions like BlackArch.
- Growing slowly improves skills and confidence.
Quick Comparison Table
| Factor | Kali Linux | Parrot OS | BlackArch Linux |
|---|---|---|---|
| User Level | Beginner+ | Beginner+ | Advanced |
| Tools Pre-installed | Extensive | Moderate | Huge collection |
| Security Features | Regular updates | Sandboxing | Minimal focus |
| Resource Usage | Moderate | Light | Heavy |
| Community Support | Strong | Good | Limited |
Final Note
Choosing the right distribution is personal. Start with clear goals. Match your skills and system power. Always test before final install. With time, you will find your best fit.
What Ethical Hacking Tools Run on Linux?
Linux supports a wide range of ethical hacking tools. These tools help in penetration testing, network analysis, and security checks. Many come pre-installed in hacking distributions. Others can be easily added later. Each tool serves a specific purpose. Learning them step by step is important. Let us explore key categories and examples below.
1. Network Scanning Tools
Network scanning tools find open ports and services. They help identify possible entry points.
- Nmap: Scans networks and detects running services.
- Angry IP Scanner: Simple tool for fast scanning.
2. Password Cracking Tools
These tools test password strength and recover lost ones.
- John the Ripper: Popular for password cracking.
- Hydra: Performs fast brute-force attacks.
3. Wireless Hacking Tools
These tools test Wi-Fi security and find weaknesses.
- Aircrack-ng: Cracks Wi-Fi keys.
- Kismet: Detects wireless networks and captures traffic.
4. Exploitation Frameworks
These tools help test known vulnerabilities.
- Metasploit: Complete framework for exploitation.
- BeEF: Focuses on browser-based attacks.
5. Sniffing and Spoofing Tools
These monitor traffic and test network defenses.
- Wireshark: Captures and analyzes network packets.
- Ettercap: Performs man-in-the-middle attacks.
6. Web Application Testing Tools
These tools test websites for vulnerabilities.
- Burp Suite: Popular tool for web app testing.
- OWASP ZAP: Open-source tool for web scanning.
7. Forensic Tools
These tools help in digital investigation.
- Autopsy: Recovers deleted files and investigates systems.
- Foremost: Extracts files from disk images.
Quick Tool Table
| Category | Tool Examples | Use Case |
|---|---|---|
| Network Scanning | Nmap, Angry IP Scanner | Find open ports, services |
| Password Cracking | John the Ripper, Hydra | Test and crack passwords |
| Wireless Hacking | Aircrack-ng, Kismet | Check Wi-Fi security |
| Exploitation | Metasploit, BeEF | Test system vulnerabilities |
| Sniffing & Spoofing | Wireshark, Ettercap | Analyze and intercept traffic |
| Web Testing | Burp Suite, OWASP ZAP | Find web flaws |
| Forensic | Autopsy, Foremost | Investigate digital systems |
Final Note
Linux makes hacking tools easy to access. Each tool has a clear role. Beginners should start with simple tools first. Gradually, move to advanced frameworks. With practice, tools become powerful allies.
How Can Beginners Start Learning Linux for Ethical Hacking?
Starting Linux may look tough for beginners. But with simple steps, the journey becomes smooth. Ethical hacking requires strong command of Linux basics. You need to know commands, file handling, and permissions. Slowly, you build confidence through practice. Step-by-step learning is the best approach. Let us go through a clear plan.
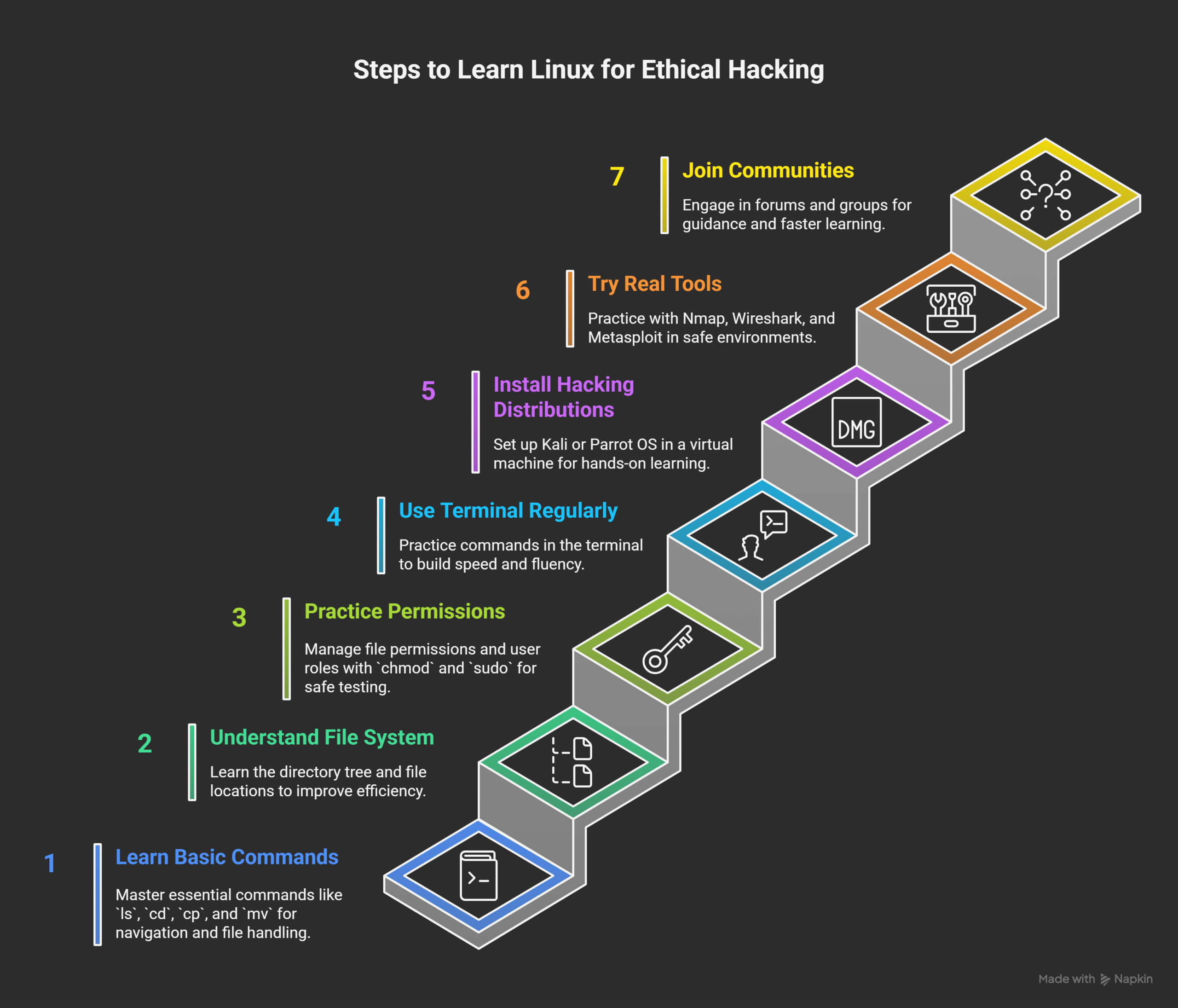
1. Learn Basic Linux Commands
- Understand navigation commands like
lsandcd. - Learn file commands like
cp,mv, andrm. - Practice with text editors like Nano or Vim.
- Repeat commands daily for quick memory.
2. Understand File System Structure
- Linux uses a tree-like file system.
- Root directory
/holds everything. - Learn where files and tools are stored.
- Knowing structure saves time in hacking.
3. Practice User and Permissions Management
- Each file has user, group, and others.
- Use
chmodto change file permissions. - Use
sudoto run admin tasks. - Permissions control system security.
4. Use Linux Terminals Regularly
- Practice in the terminal, not just GUI.
- Learn shortcuts for faster command use.
- Keep using commands daily for fluency.
- Comfort with terminal is essential for hacking.
5. Install a Hacking Distribution
- Choose Kali or Parrot for beginners.
- They come with many tools pre-installed.
- Install on a VM to avoid risks.
- Safe testing makes learning stress-free.
6. Try Real Hacking Tools
- Start with Nmap for network scanning.
- Use Wireshark for traffic analysis.
- Explore Metasploit for simple exploits.
- Tools bring real hacking experience.
7. Join Online Communities
- Forums provide solutions to common issues.
- Kali forums and Reddit are helpful.
- Communities share tutorials and challenges.
- Networking helps faster learning.
Beginner Learning Table
| Step | Focus Area | Example Tools/Commands |
|---|---|---|
| Basic Commands | File, folder handling | ls, cp, mv |
| File System | Structure and locations | /etc/, /home/ |
| Permissions | User roles, rights | chmod, sudo |
| Terminals | Practice shell use | Bash, Zsh |
| Distribution | Install preloaded OS | Kali, Parrot |
| Hacking Tools | Simple tool practice | Nmap, Wireshark |
| Community | Join forums, groups | Kali Forums, Reddit |
Final Note
Beginners must start simple and practice daily. Commands, permissions, and structure are foundation. Virtual machines give a safe practice ground. Tools add practical hacking skills. With steady steps, Linux mastery comes naturally.
How Does Entri’s Cybersecurity Course Teach Linux for Ethical Hacking?
Entri’s team studied the growing digital threat landscape. We found rising cyberattacks as the biggest challenge today. That is why we built our AI-powered Cybersecurity Course. It gives learners a strong foundation in Linux for hacking. The course follows a hybrid mode for flexible learning. Learners gain both theory and hands-on practice. This approach makes Linux easy and practical.
Strong Linux Foundation
- The course begins with Linux command basics.
- File handling and permissions are taught step by step.
- Learners explore Linux structure for cybersecurity needs.
- This builds confidence with system-level operations.
Hands-On Ethical Hacking Training
- Tools like Nmap, Wireshark, and Metasploit are covered.
- Learners practice in safe lab environments.
- Real-world scenarios are simulated in guided sessions.
- Practice builds skill and problem-solving ability.
Hybrid Learning Model
- Course blends online and offline learning modes.
- Learners get recorded video lectures for flexibility.
- Mentor-led sessions provide interactive guidance.
- Hands-on labs ensure 80% practical exposure.
AI-Powered Personalization
- AI adapts content to learner pace and skill.
- Beginners progress steadily with tailored guidance.
- Advanced learners explore deeper tools and concepts.
- This ensures every learner benefits fully.
Certifications and Recognition
- Learners get Entri Level Certification on completion.
- NSDC certification adds national recognition.
- Illinois Tech certification gives international weight.
- Internship certification boosts industry readiness.
Placement and Career Support
- Placement team connects learners with job opportunities.
- Resume reviews help showcase Linux and hacking skills.
- Guidance comes from mentors at top global firms.
- Over 3000+ learners have already secured placements.
Course Highlights Table
| Feature | Details |
|---|---|
| Learning Mode | Hybrid (Online + Offline) |
| Duration | 9 months + 1-month internship |
| Focus Areas | Linux, Cybersecurity, Ethical Hacking |
| Practical Exposure | 80% hands-on training |
| Certifications | Entri, NSDC, Illinois Tech |
| Career Support | Resume help, job guidance, placement |
Final Note
Entri’s Cybersecurity Course makes Linux hacking simple and structured. Learners master commands, tools, and real scenarios. Hybrid learning ensures both flexibility and mentorship. With global certifications, your skills get industry value. Placement support makes your career path stronger.
What Career Benefits Come from Learning Linux for Ethical Hacking?
Linux is the backbone of ethical hacking careers today. Most hacking tools and frameworks run best on Linux. Companies prefer professionals skilled in Linux systems. Mastery of Linux makes candidates more competitive in the job market. Ethical hackers with Linux skills handle networks, servers, and security better. With rising cyber threats, demand keeps growing. Let’s see how Linux skills boost careers.
High Demand Across Industries
- Banks need Linux professionals for data security.
- Healthcare protects patient data with Linux experts.
- Startups use ethical hackers to test apps.
- Government agencies hire to secure national systems.
Better Job Opportunities
Linux opens doors to multiple roles.
- Penetration Tester: Tests systems for vulnerabilities.
- Security Analyst: Monitors and investigates attacks.
- Network Security Engineer: Secures company networks.
- Forensic Expert: Investigates digital evidence.
Global Certifications Advantage
Linux knowledge supports top certifications.
- CEH (Certified Ethical Hacker) needs Linux basics.
- CompTIA Security+ requires Linux practice.
- OSCP (Offensive Security) tests on Linux labs.
- Certifications add strong value to resumes.
Higher Salary Growth
- Linux professionals earn higher than average IT roles.
- Demand exceeds supply, raising salaries further.
- Ethical hackers enjoy global job opportunities.
- Skills ensure long-term career stability.
Strong Placement Support from Courses
- Courses like Entri’s give placement help.
- Resume reviews highlight Linux and hacking expertise.
- Interview guidance prepares learners for tough questions.
- Hiring partners provide direct job access.
Quick Career Benefits Table
| Benefit Area | Impact of Linux Skills |
|---|---|
| Job Roles | Penetration Tester, Analyst, Engineer |
| Certifications | CEH, OSCP, CompTIA Security+ |
| Industries | Banking, Healthcare, Startups, Government |
| Salary | Higher than average IT salaries |
| Career Growth | Global demand, stable opportunities |
Final Note
Linux mastery creates endless opportunities in cybersecurity. It powers job readiness and certifications. Industries trust Linux experts for stronger defenses. With skills and certifications, salaries rise quickly. Learning Linux is a career investment with lifelong rewards.
Conclusion
Linux is the core skill for ethical hackers today. It powers tools, commands, and secure environments. With Linux, hackers test networks and protect data effectively. Learning it step by step builds strong hacking skills. Courses make this journey easier with guided practice. Real-world labs give safe hands-on exposure. Certifications add global recognition to your profile.
Understanding Why Linux Is Essential for Ethical Hacking shapes your career path. It opens doors to jobs in every industry. Companies value professionals skilled in Linux security. Salaries and opportunities grow with strong Linux knowledge. Ethical hacking becomes both a passion and a profession. Start now and grow your skills consistently. Linux mastery will secure your digital future.
| Related Articles | |
| Entri Launched AI-Powered Cybersecurity Course | Cybersecurity Career Path |
| An Introduction to Cybersecurity Ethics | Top Cybersecurity Languages to Learn |
Frequently Asked Questions
Why is Linux preferred for ethical hacking?
Linux offers open-source access for learning and practice. Most ethical hacking tools run better on Linux. It provides strong security features and customization options. Ethical hackers rely on its flexibility and command-line power. These features make Linux the first choice for hacking.
Can beginners learn Linux for ethical hacking?
Yes, beginners can easily start with basic Linux commands. Many hacking distributions are beginner-friendly, like Kali and Parrot. Courses guide learners step by step with practice labs. Virtual machines help beginners test without system risk. Daily practice builds confidence and real hacking skills.
Which Linux distribution is best for hacking?
Kali Linux is the most popular for ethical hacking. It comes with many pre-installed hacking tools. Parrot OS is another great beginner-friendly option. BlackArch Linux suits advanced learners needing large toolsets. The choice depends on skills, goals, and system requirements.
What skills should I learn first on Linux?
Start with basic navigation and file handling commands. Learn user permissions and how sudo works. Explore the Linux file system step by step. Practice using the terminal instead of GUI tools. These basics prepare you for hacking tools later.
Do companies value Linux skills for cybersecurity jobs?
Yes, companies highly value Linux skills in cybersecurity roles. Many servers and networks run on Linux systems. Ethical hackers with Linux knowledge handle real threats better. Linux also supports certifications like CEH and OSCP. This makes candidates more competitive in the job market.
Can Linux skills increase my salary opportunities?
Yes, Linux expertise leads to higher salary offers. Ethical hackers with Linux experience are in high demand. Industries like banking and healthcare hire Linux professionals regularly. Global certifications further raise earning potential significantly. Strong Linux skills ensure long-term career growth.
How does Entri’s Cybersecurity Course teach Linux?
Entri’s course starts with Linux basics and commands. Learners then practice with hacking tools like Nmap. Hybrid learning combines recorded lectures with live mentor sessions. Safe labs give 80% hands-on training experience. Global certifications and placement support boost career readiness.
How long does it take to learn Linux for ethical hacking?
Learning Linux basics can take a few weeks. Mastering hacking tools may require a few months. Consistent practice improves speed and understanding of commands. Courses like Entri’s guide learners efficiently and safely. Real-world labs accelerate learning through practical exposure.
Do I need prior programming knowledge to use Linux?
No, beginners can start without prior programming knowledge. Basic command-line skills are enough to get started. Learning scripting like Bash helps in advanced hacking later. Courses teach programming alongside Linux tools step by step. This ensures smooth progression for all learners.
Can Linux skills help me switch to a cybersecurity career?
Yes, Linux knowledge is crucial for cybersecurity transitions. Employers look for Linux-proficient candidates in security roles. Ethical hacking skills combined with Linux open many job paths. Certifications further validate your skills to recruiters. With practice, Linux mastery can secure your career future